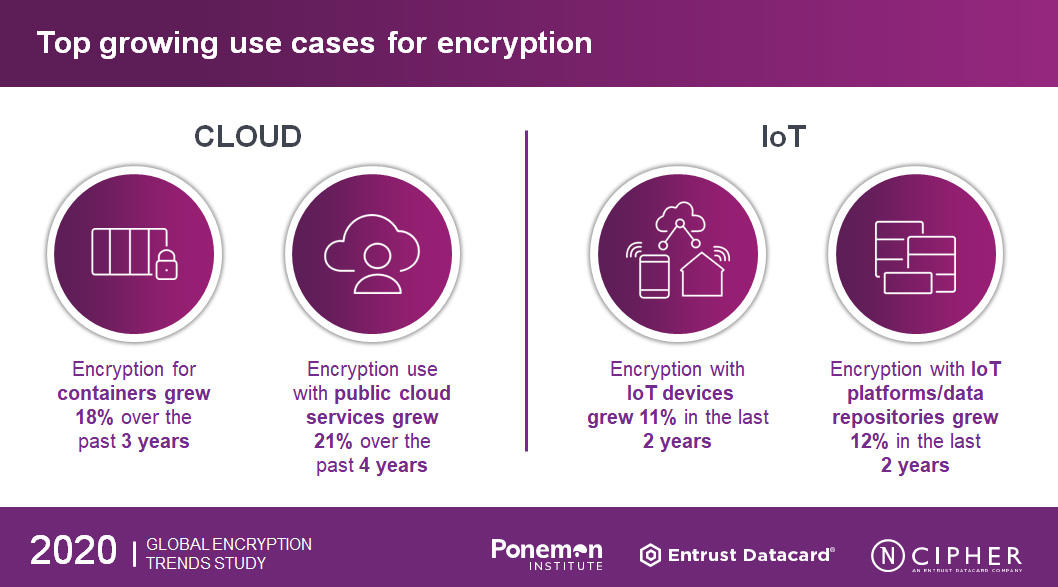
Many organizations are adopting new digital initiatives, IoT and cloud, but are also embracing encryption to protect their applications and sensitive information. A successful strategy discovers where is the most sensitive data in the organization and develops a secure cloud storage system for it.
Organizations are putting more sensitive data in the cloud. According to the 2020 Global Encryption Trends Study, forty-five percent of respondents who are encrypting their data say encryption is performed on-premises prior to sending data to the cloud using keys their organization generates and manages. However, 36 percent of respondents perform encryption in the cloud, with cloud provider generated/managed keys. Those storing sensitive data in the cloud and not protecting it at all through encryption or otherwise making it unreadable are in multiple forms of jeopardy. The organizations are taking a risk when not protecting, because when their data is breached, and the probability is that it will be, they will be forced by data breach disclosure laws to report the breach to those whose data has been stolen.
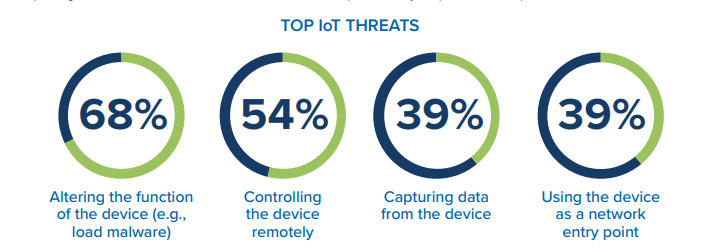
IoT (Internet of Things) refers to the billions of physical devices around the world that are now connected to the internet, all collecting and sharing data. Thanks to the wireless networks, it’s possible to turn anything, from something as small as a pin o something as big as a car, into a part of the IoT. The Internet of Things is making the world more smarter and responsive, merging digital and physical worlds. The benefits of IoT for business is that enterprises should have access to more data about their own products and their own internal systems, and a greater ability to make decisions as a result. With more people and more information involved, threats landscape is growing.
Not only businesses are at threat, but also consumers of Internet-connected household devices are also at risk. Once connected devices are deployed in the field, they become attractive targets for criminal actors to:
– expose protected content stored on or transmitted by the device,
– use the device’s trusted status to gain access to other connected systems or
Cybercriminals or insiders with privileged access can use unsecured processes to produce counterfeits and clones, and so decrease revenues and damage brand reputation of manufacturers.
Even though the challenges are greater, there are ways to protect organizations sensitive data and information and solve problem using encryption. Best practices for IoT data security must include using encryption solutions that adapt based on the type of environment that they are encrypting. IoT data protection solutions must span edge to cloud, provide scalable encryption and key management.
IoT is becoming a major driver for the use of PKI (Public Key Infrastructure). There is growing recognition that PKI provides important core authentication technology for the IoT.
Using HSMs and supporting security applications to create and protect the underlying keys, IoT devices can be manufactured with unique, cryptographically-based identity that is authenticated when a connection to gateway or central server is attempted. With this unique ID at place, you can track each device throughout its lifecycle, communicate securely with it and prevent it from executing harmful processes.
Establishing strong authentication is just one part of the problem. The IoT demands large scale management and protection of digital certificates and the underlying keys and support for multiple key algorithms, and are supported by a well-designed public key infrastructure (PKI). The accepted PKI best practice to secure your most sensitive keys and business processes it to use an HSM.
A basic principle of any kind of security is that once something is locked, the more control you have over the key to the lock, the more control you have over the overall security of what’s behind the lock. If your cloud provider manages your keys, you are adding another threat vector to your data security. This is why it is best practice to manage your own keys using hardware security modules (HSMs).