Overall cybersecurity attacks are increasing multiple ways. And the only way you can really address this situation is through technology and automation. Security has always been challenging but add to that the fact that we have a serious shortage overall in the market of qualified people. And infrastructure continues to evolve rapidly. The only way we’re going to get the bad guys is by leveraging technology, leveraging automation. The great way to do that is using security automation.
Companies moving to the cloud have embraced automation. And they have seen clear results—for instance, they’re able to use their resources more efficiently and save money. If a load goes up, the number of machines will increase automatically. When the load goes down, a bunch of machines are automatically killed. So, their costs are reduced.
We always had an IT function where the operations people were deploying. Developers wrote code and IT did the deployment. Then in development, things started going way faster than deployment. At some point, they decided to deal with it, understanding that business needed to move fast. So developers started writing automation into their code. And that revolution came about and so we have developers who basically write how things should work in production. That’s how DevOps came about.
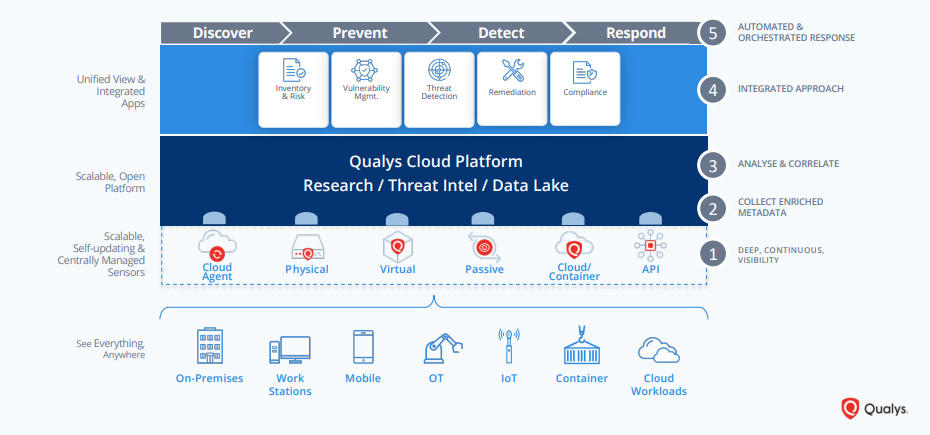
The solution is Qualys Cloud Platform
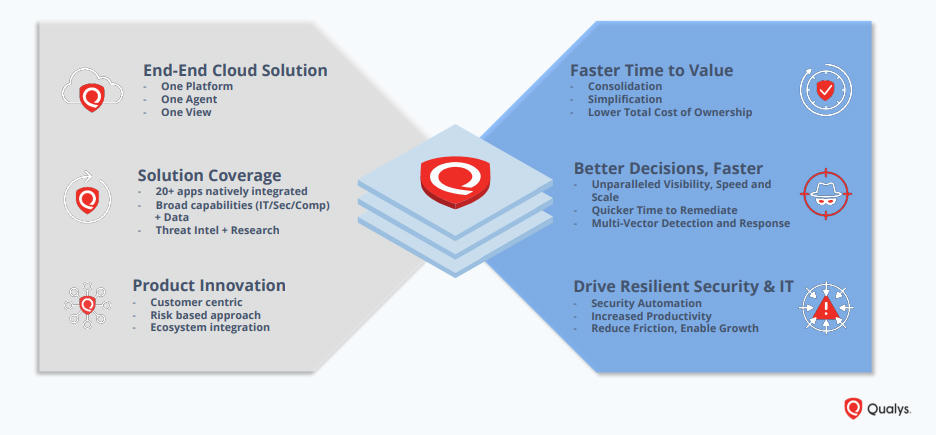
It provides an end-to-end solution, allowing you to avoid the cost and complexities that come with managing multiple security vendors. The Qualys Cloud Platform automatically gathers and analyzes IT, security, and compliance data in a scalable, state-of-the-art backend. Provisioning any of Qualys’ natively integrated security and compliance apps – twenty and counting – is as easy as checking a box.
Qualys Cloud Platform is accessible directly in the browser, no plugins necessary. And with a powerful dashboard, security and compliance pros and managers get a complete and continuously updated view of all of their IT assets — from a single-pane-of-glass interface.
It’s a fully customizable dashboard that lets you see the big picture, drill down into details, and generate reports for teammates and auditors. Its intuitive and easy-to-build dynamic dashboards aggregate and correlate all of your IT, security and compliance data in one place from all the various Qualys Cloud Apps. With its powerful elastic search clusters, you can now search for any asset – including on-premises, endpoint and cloud assets – with 2-second visibility.
Advantages of our cloud-based architecture:
– No hardware to buy or manage
Nothing to install or manage, and all services are accessible on the cloud via web interface. Qualys operates and maintains everything.
– Easy global scanning
Easily perform scans on geographically distributed and segmented networks both at the perimeter, behind the firewall, on dynamic cloud environments and endpoints.
– Up-to-date resources
Qualys has the largest knowledge base of vulnerability signatures in the industry, and performs over 6 billion IP scans per year. All security updates are made in real time.
– Lower operating costs
With everything in the cloud, there are no capital expenditures, no extra human resources needed, and no infrastructure or software to buy and maintain.
– Seamless scaling
Qualys Cloud Platform is a scalable, end-to-end solution for all aspects of IT security. Once deployed, seamlessly add new coverage, users and services as you need them.
– Securely stored data
Vulnerability data securely stored and processed on an n-tiered architecture of load-balanced servers. Our encrypted databases are physically and logically secure.
Ask us more about Qualys Cloud Platform!