Digital environments allow us to explore and develop new services and products to meet changing user needs to match way they live, work and use technology. Also, fast changing digital environment gives customer competitive advantage and improves effectiveness and operational efficiency of an enterprise ensuring the high quality of its products, service and support.
But that fast moving environment multiplies the security risks. Those emerging technologies -cloud, IoT, blockchain, digital payments need secure cryptographic solutions. While the blockchain technology that underpins distributed ledgers has proven in itself to be very secure, there are many questions about how to protect both the cryptographic keys that allow access to the ledger and blockchain applications.
Blockchain is rising up agenda for many organizations. It is a system of recording information that makes it impossible to change, cheat or hack the system. The technology has the potential to transform the way data is shared and value is transferred.
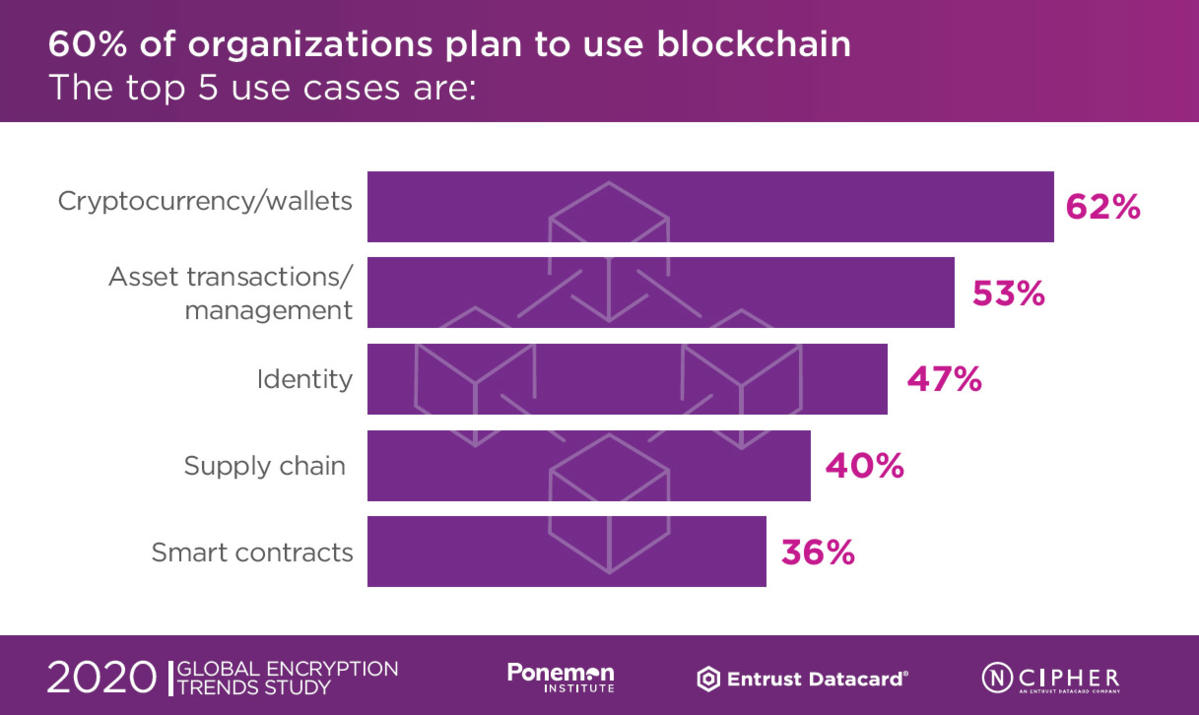
Most companies plan to use blockchain. Sixty percent of respondents say their organizations.will use blockchain. The two primary use cases. are for cryptocurrency/wallets and assettransactions/management.
Also, if this technology is to be adopted in financialn trades, payments, health care, but also of government and regulatory applications, there will be no longer security risks.
HSM
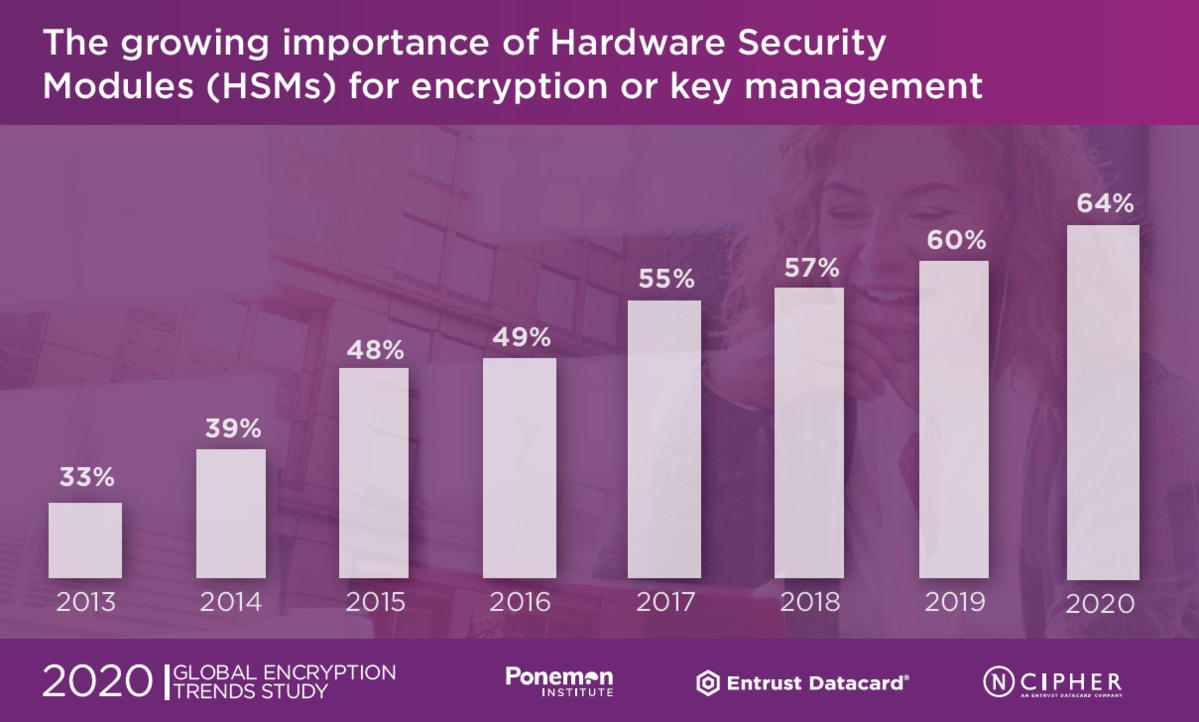
An HSM (hardware security modules)is a crypto-processor that securely generates, protects, and stores keys. Nowadays, security-conscious organizations and institutions use HSM to manage their digital keys, protect potential access points that require secure, verified digital signatures. The overall average importance rating for HSMs as part of an encryption and key management strategy in the current year is 64 percent.
Reasons an HSM is secure and trusted:
– it is built on top of specialized hardware, which is well-tested and certified.
– it has a security-focused OS
– Has limited access via a network interface that is strictly controlled by internal rules
– Actively hides and protects cryptographic material
A successful blockchain system needs highly reliable methods of interfacing with the strong key protection practices afforded by HSMs, and these HSMs must deliver the scaling and flexibility a decentralized blockchainmodel needs.
Blockchain combines message and asset in one token. Once an asset is embedded into a blockchain or distributed ledger, possessing the associated cryptographic keys is the only way to retrieve or move the asset. In other words, the key becomes the asset. For example, in a traditional IT model, a key protects the database, which in turn protects the data or the asset. When the key and the asset are one and the same, anyone who obtains the key can monetize and exploit the asset instantly.
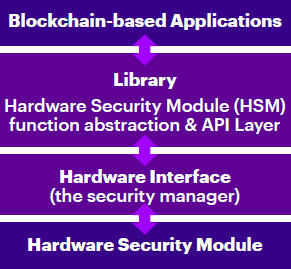
So, the solution follows a patent-pending, general-purpose approach in creating a library that helps integrate hardware security devices with blockchain technology. The library connects an HSM to a security manager, whose role is to manage the encryption and decryption of sensitive client data. The library allows users to write blockchain business applications at the top that are then implemented as blockchain applications in the middle layer. After that, they are integrated with hardware so that all keys are stored securely inside an HSM device. Once keys are created and stored in an HSM architecture, they are essentially impossible for unauthorized users to extract.
Find out more at – https://tinyurl.com/y75qvj26 or contact us – https://alfatec.hr/kontakt/