Organizations are constantly on the search for solutions to improve the security of their systems, as cybercriminals can exploit even the slightest vulnerability.
For this reason, organizations deploy Risk-Based Vulnerability Management Tools, which successfully detect and generate reports of detected vulnerabilities.
About Vulnerability management
It is an important part of any cybersecurity strategy. It involves proactive assessment, prioritization and treatment, as well as a comprehensive report of vulnerabilities within IT systems. Vulnerability management identifies IT assets and compares them to a constantly updated vulnerability database to spot threats, misconfigurations and weaknesses. Vulnerability management should be done regularly to avoid cybercriminals exploiting vulnerabilities in IT systems, which could lead to service interruptions and costly data breaches.
With so many vulnerabilities present in large, complex and interconnected computing environments, enterprises cannot practically implement all software patches and other remediations on a timely basis, if at all.
Risk-based vulnerability management (VM) tools provide IT security teams with a continuous, automated ability to identify, prioritize and remediate cyber-based vulnerabilities according to the relative risk they pose to a specific organization.
A complex process of triage that quickly identifies and escalates the vulnerabilities that present the most risk in an organization’s particular circumstances is required. This takes automated tools with machine learning (ML) capabilities. The leading vulnerability management software providers are adapting by incorporating risk-based solutions into their products.
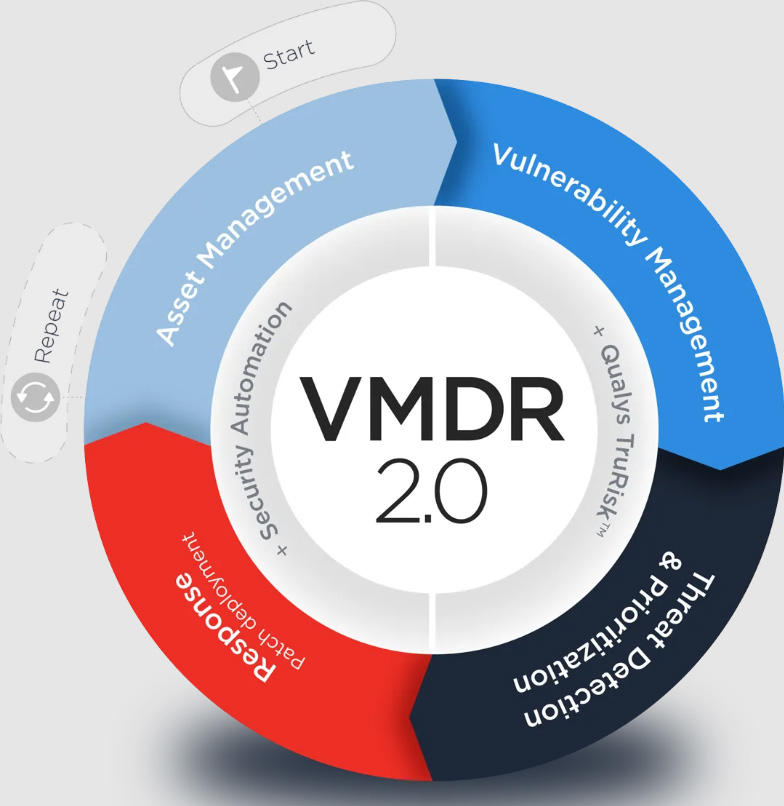
Qualys VMDR
Qualys VMDR (Vulnerability Management, Detection and Response) automatically discovers and inventories all software and hardware assets wherever they are in an environment. This cloud-based app continuously assesses vulnerabilities and applies threat intelligence to prioritize and fix actively exploitable vulnerabilities.
Key differentiators include real-time threat intelligence linked to machine learning to control and respond to evolving threats and prevent breaches. The solution also automatically detects and deploys the latest superseding patch for the vulnerable asset. In addition to vulnerabilities, it lists critical misconfigurations. It covers mobile devices as well as operating systems and applications. It offers virtual scanners, network analysis and other tools in a single app unified by orchestration workflows.
The product is highly rated by IDC, TrustRadius and G2. IDC numbers show that Qualys boasts about a 20% share of the market. Users speak well of the quality and range of coverage of its vulnerability signature databases. Users also cite its ability to detect vulnerabilities and configuration issues and react in real time, its ability to organize security policy, and its good reporting and alerting mechanisms.
Ask us for personal demonstration of Qualys VMDR 2.0 with TruRisk solution!