For decades, enterprise data encryption and effective key management were something most enterprises wanted to do but couldn’t — if they tried to do it at all. Only the largest of enterprises with the most mature security teams even attempted it.
Fortunately, that’s now starting to change for the better. But this progress comes at a time when new challenges are emerging; the complexity of enterprise environments is growing as data is spread across on-premises systems and various cloud services.
2021 Global Encryption Trends Study is the most comprehensive encryption survey in the industry, highlights how organizations are managing encryption strategies and data security threats across multiple clouds.
Coverage includes:
– Multi-cloud encryption strategies;
– Trends in encryption adoption and deployment choices;
– Threats, drivers, and priorities;
– Importance of hardware security modules (HSMs).
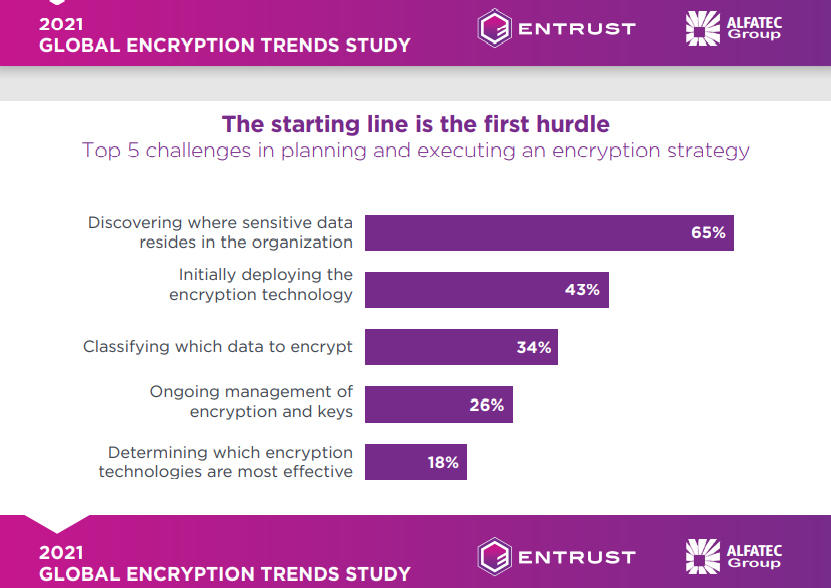
It is hard to encrypt sensitive data when security teams don’t know where that data resides. In a new 2021 Global Encryption Trends Study from Ponemon Institute and Entrust, 65% of organizations polled said that discovering where their sensitive data actually resides is their top enterprise data encryption challenge. Still, a historically high percentage of enterprises now have an enterprise encryption strategy, with 50% of respondents claiming to have such a strategy and that it is being consistently applied. Still, a sizable minority of 37% report they have a much more limited encryption strategy and effort in place. Overall, it is good news, considering that in 2006 only 15% of enterprises had an encryption strategy that was applied consistently across their enterprise.
Those findings mirror a 2019 nCipher Security (recently purchased by Entrust) survey that found 45% of 5,800 respondents said their encryption strategy is applied consistently throughout the enterprise. That survey found the biggest threats to data were employee carelessness (54%), outside attackers (30%) and insider threats (21%).
Perhaps one of the biggest challenges, in addition to complex cloud and on-premises environments, is the increase in the number of encryption tools enterprises are using. According to the report, organizations use an average of eight different encryption products, and unified key management across cloud services and enterprise environments were ranked important to very important by 45% of respondents.
While technology changes in cloud computing have added complexity to enterprise environments in some areas, technology changes in hardware — notably hardware security modules (HSMs) — are helping enterprises to manage their encryption and key management strategies more effectively. Sixty-six percent of respondents said HSMs are central to their encryption and key management strategies. That figure is expected to grow to 77% within a year.
Currently, 61% of survey respondents said their company centrally manages cryptography services within their organization, while 39% said that each individual team owns the management of HSMs as well as other cryptographic responsibilities.
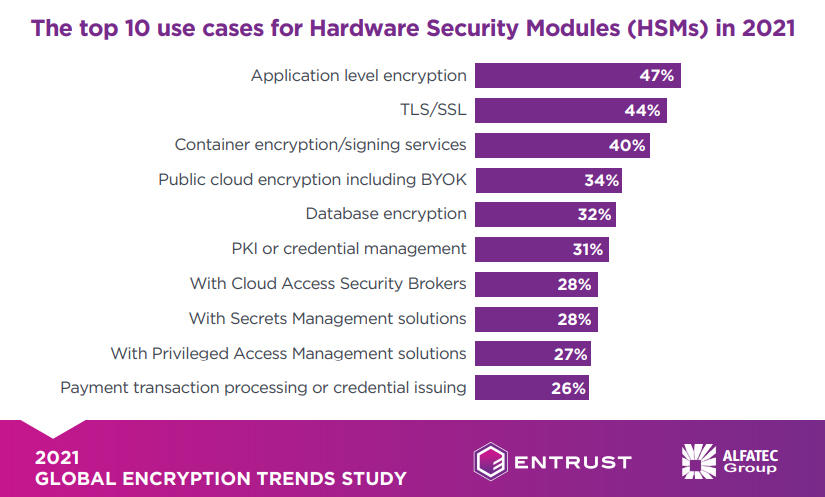
The HSMs may help simplify cloud encryption and key management difficulties. The study found that application encryption (47%) and TLS/SSL (44%) are the two most popular reasons to use HSMs, with signing services for containers coming in at 40%.
Much about enterprise encryption has changed over the years, there are many aspects that have remained the same; the importance of system performance and latency, ease of key management and policy enforcement capabilities remained the most important features of encryption products and services. Also, the survey found payment data and financial records are the types of data most commonly encrypted. Surprisingly, healthcare data was among the least likely data to be encrypted.
Ask us more about 2021 Global Encryption Trends Study!