Vulnerability is a security weakness in a computer system that permits unauthorized or unwelcome access. For example, an Internet browser could have a vulnerability that crashes the browser or grants someone else access to files on your computer when you visit their site. Whether it is on an operating system, a processor, a server, an application, all companies are exposed to the exploitation of their vulnerabilities. To face new threats, companies must equip themselves according to their infrastructures (traditional, virtualized, Cloud, hybrid) and their needs.
We present Qualys VMDR “Vulnerability Management” solutions to respond to the market and the breach management problem. A vulnerability assessment is a risk management process used to identify, quantify and rank possible vulnerabilities to threats in a given system.
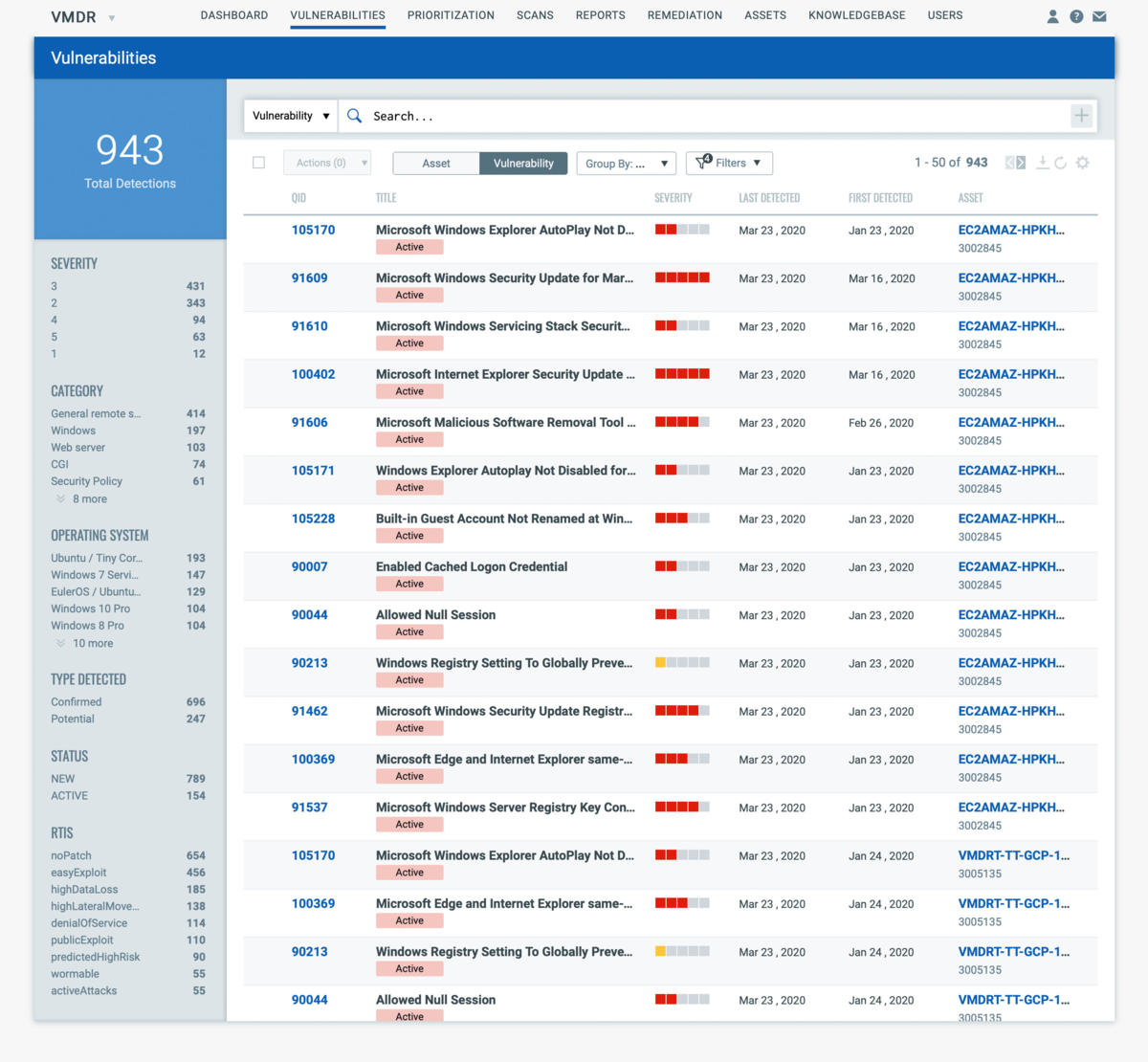
Qualys VMDR enables organizations to automatically discover every asset in their environment, including unmanaged assets appearing on the network, inventory all hardware and software, and classify and tag critical assets. VMDR continuously assesses these assets for the latest vulnerabilities and applies the latest threat intel analysis to prioritize actively exploitable vulnerabilities.
Finally, VMDR automatically detects the latest superseding patch for the vulnerable asset and easily deploys it for remediation. By delivering all this in a single app workflow, VMDR automates the entire process and significantly accelerates an organization’s ability to respond to threats, thus preventing possible exploitation.
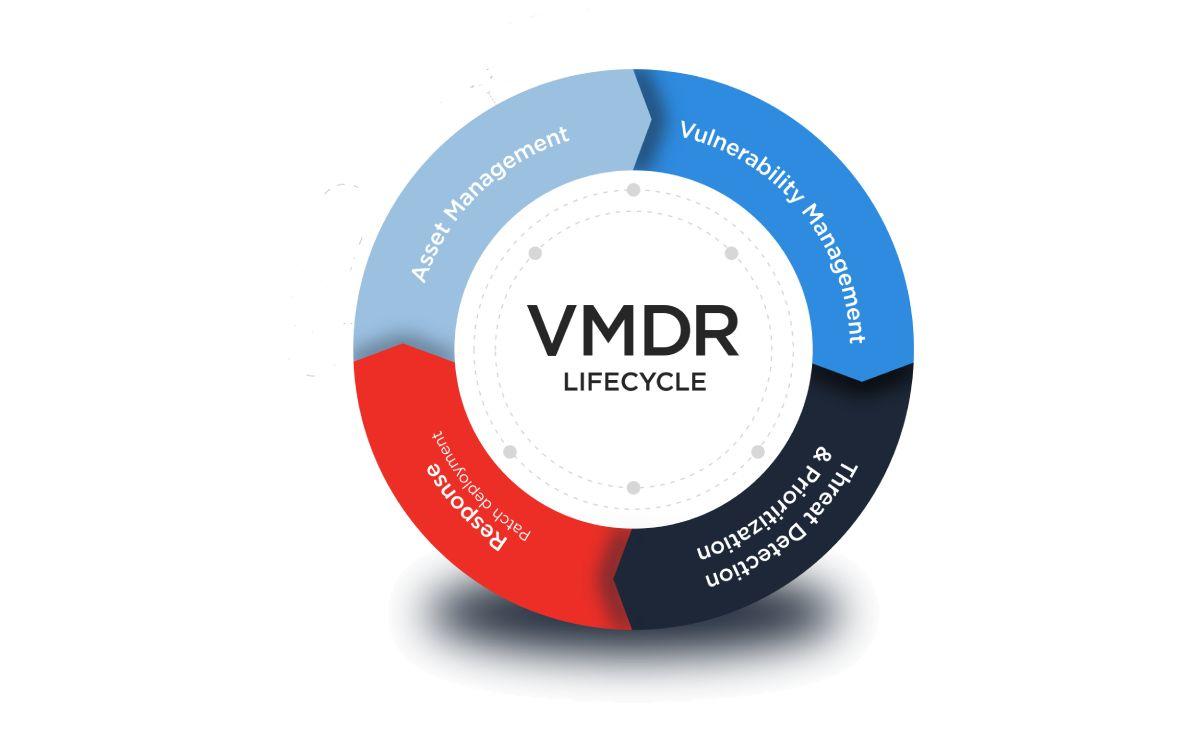
This all-in-one app, built from the ground up, brings together:
1. ASSET MANAGEMENT (Identify all assets (known and unknown) that connect to the network—on prem, endpoints, clouds, containers, mobile, OT and IoT—for a comprehensive, categorized global IT asset inventory that’s always up to date)
Apps and services:
Asset Inventory
– On-premises Device Inventory – Detect all devices and applications connected to the network including servers, databases, workstations, routers, printers, IoT devices, and more.
– Certificate Inventory – Detect and catalog all TLS/SSL digital certificates (internal and external facing) from any Certificate Authority.
– Cloud Inventory – Monitor users, instances, networks, storage, databases and their relationships for a continuous inventory of resources and assets across all public cloud platforms.
– Container Inventory – Discover and track container hosts and their information – from build to runtime.
– Mobile Device Inventory – Detect and catalog Android, iOS/iPadOS devices across the enterprise, with extensive information about the device, its configurations, and installed apps.
Asset Categorization and Normalization
Gather detailed information, such as an asset’s details, running services, installed software, and more. Eliminate the variations in product and vendor names and categorize them by product families on all assets.
2. VULNERABILITY MANAGEMENT (Identify vulnerabilities and misconfigurations in real-time across your entire hybrid environment)
Configuration Assessment
Assess, report and monitor security-related misconfiguration issues based on the Center for Internet Security (CIS) benchmarks.
Certificate Assessment
Assess your digital certificates (internal and external) and TLS configurations for certificate issues and vulnerabilities.
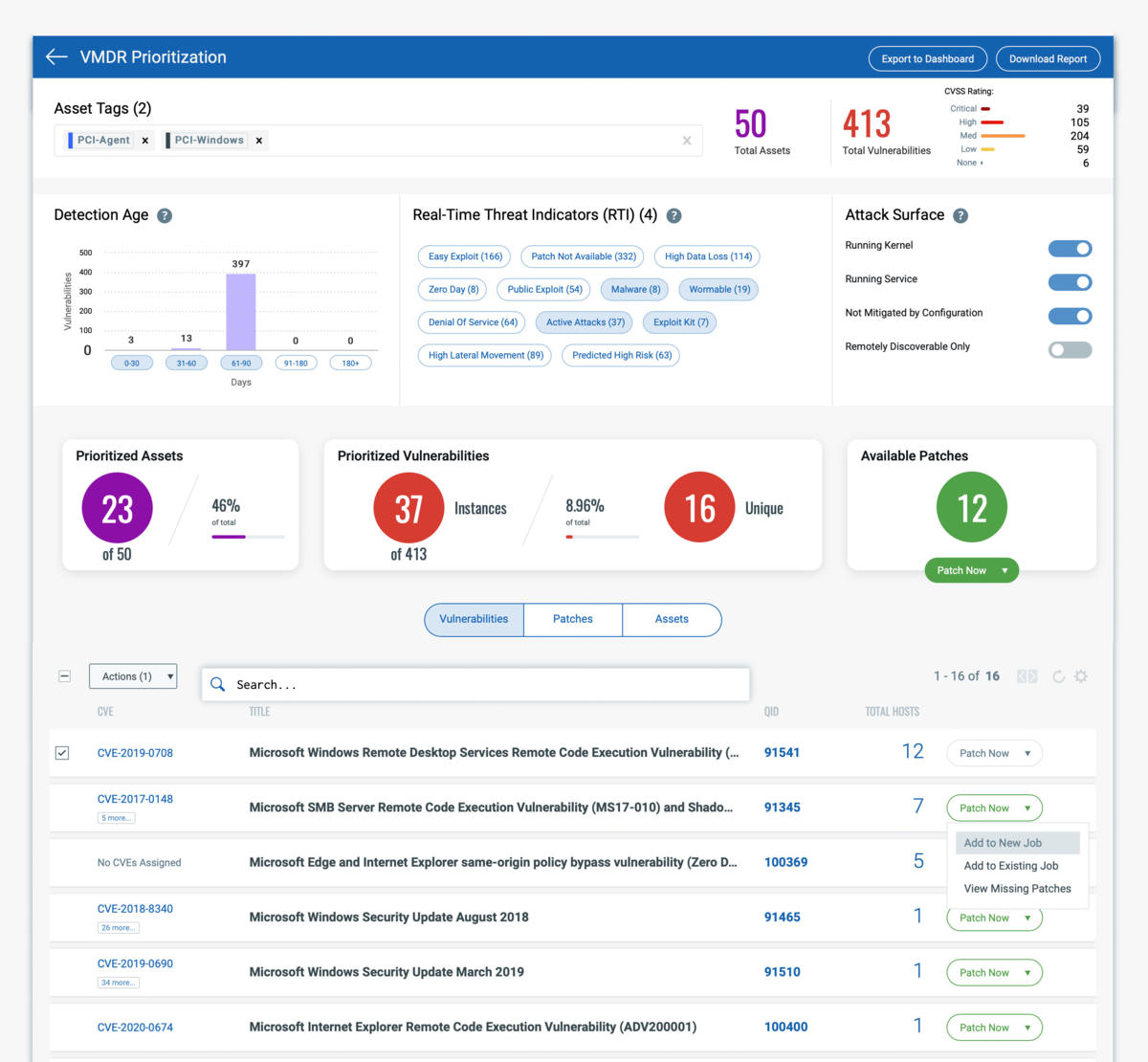
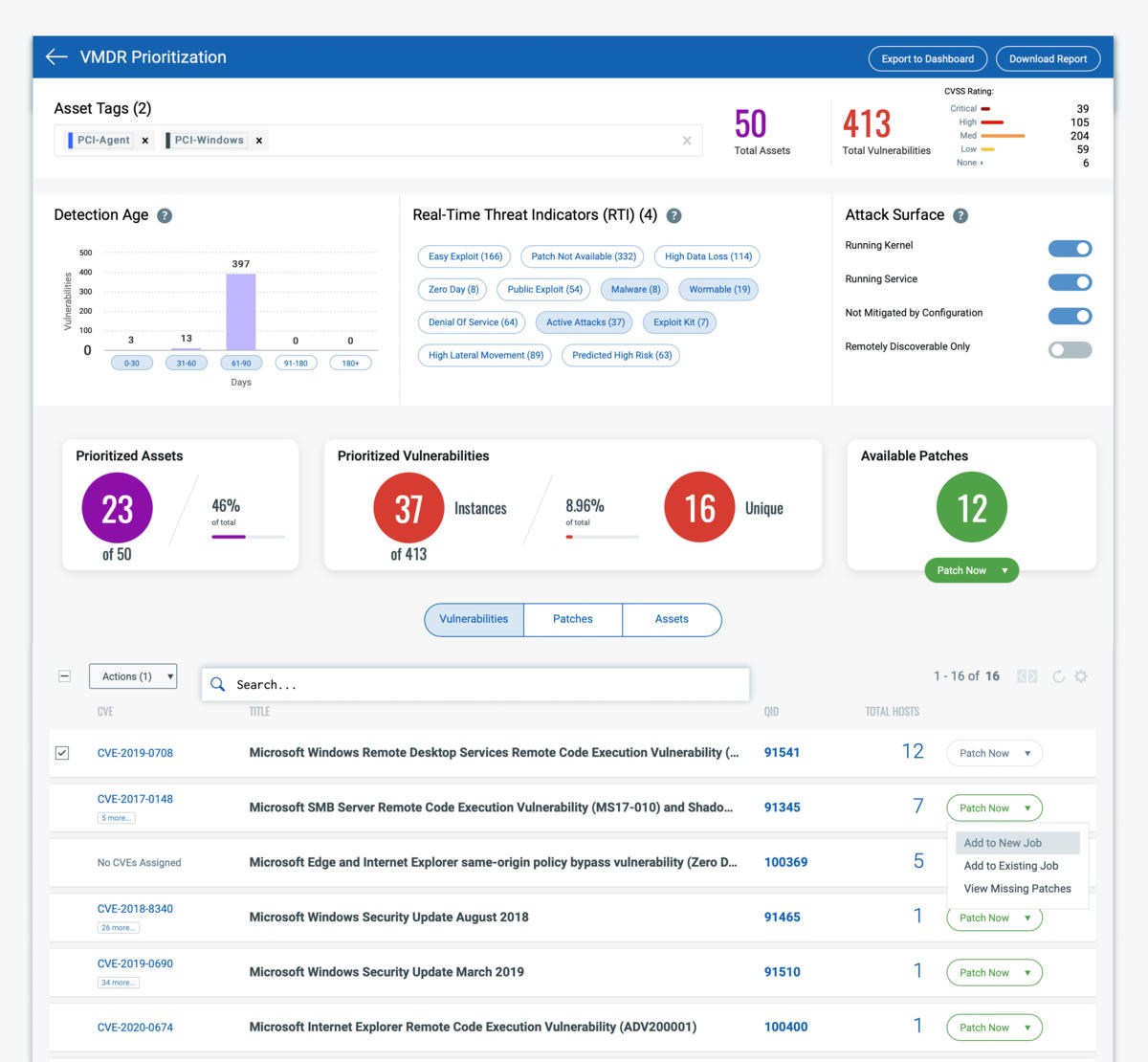
3. THREAT DETECTION & PRIORITIZATION (Automatically prioritize the vulnerabilities posing the greatest risk to your organization using advanced correlation and machine learning)
Continuous Monitoring
Alerts you in real time about network irregularities. Identifies threats and monitors unexpected network changes before they turn into breaches.
Threat Protection
Pinpoint your most critical threats and prioritize patching. Using real-time threat intelligence and machine learning, take control of evolving threats, and identify what to remediate first.
4. RESPONSE (PATCH DEPLOYMENT) – With a single click, globally deploy the most relevant superseding patch, or quarantine vulnerable assets.
Automatically correlate vulnerabilities and patches for specific hosts, decreasing your remediation response time. Search for CVEs and identify the latest superseding patches.
Keeping your system up to date is essential. Not all vulnerabilities are exploited quickly, but your company cannot take the risk. Once you know your vulnerabilities and which ones or the most dangerous for your business, patch vulnerabilities as fast as you can.
Dealing with Vulnerability Management issues? Ask us for personal demonstration of Qualys VMDR!