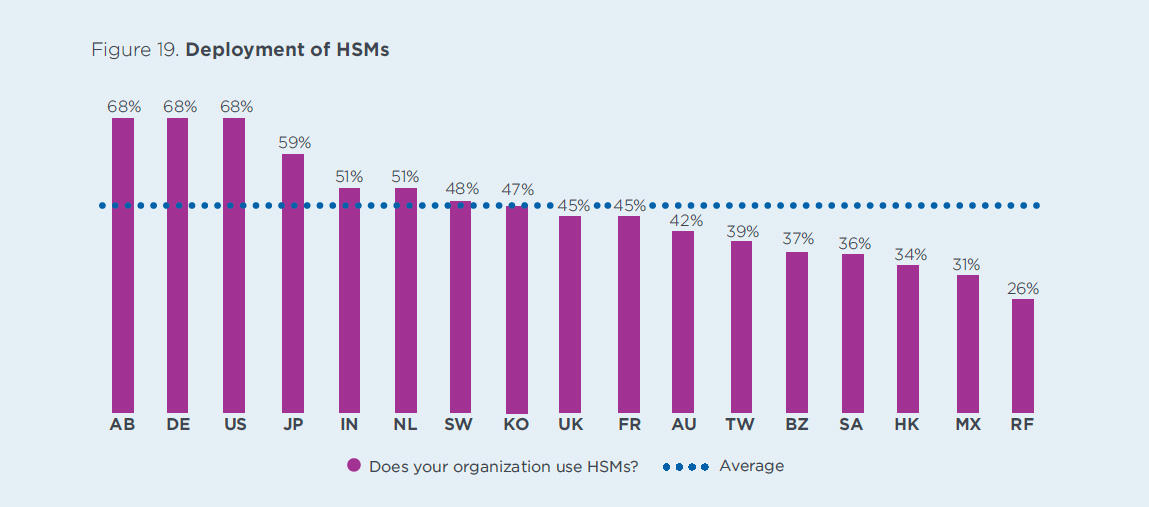
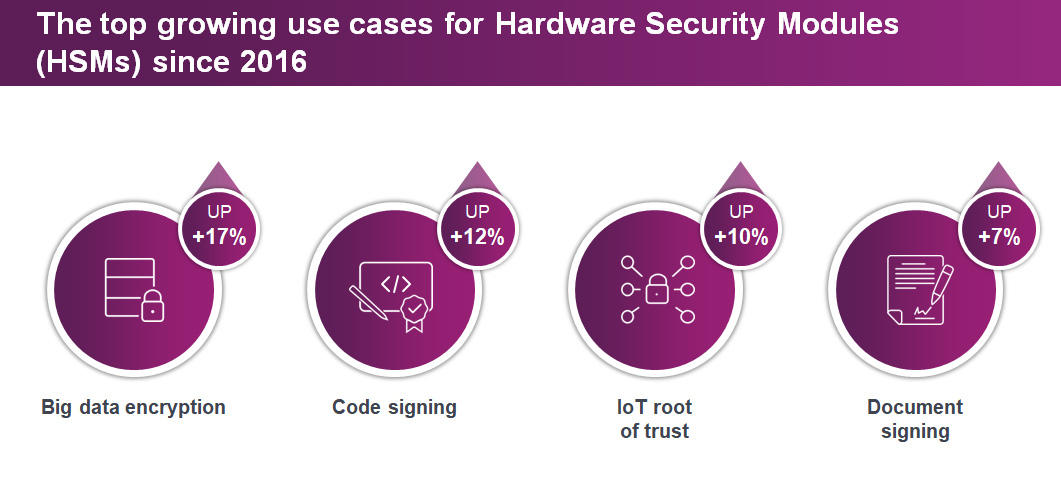
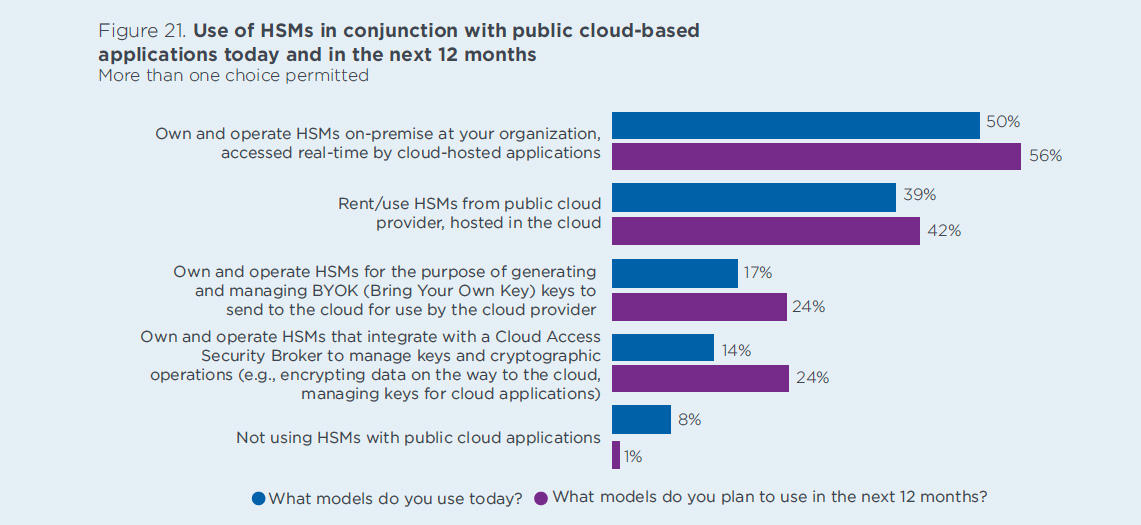
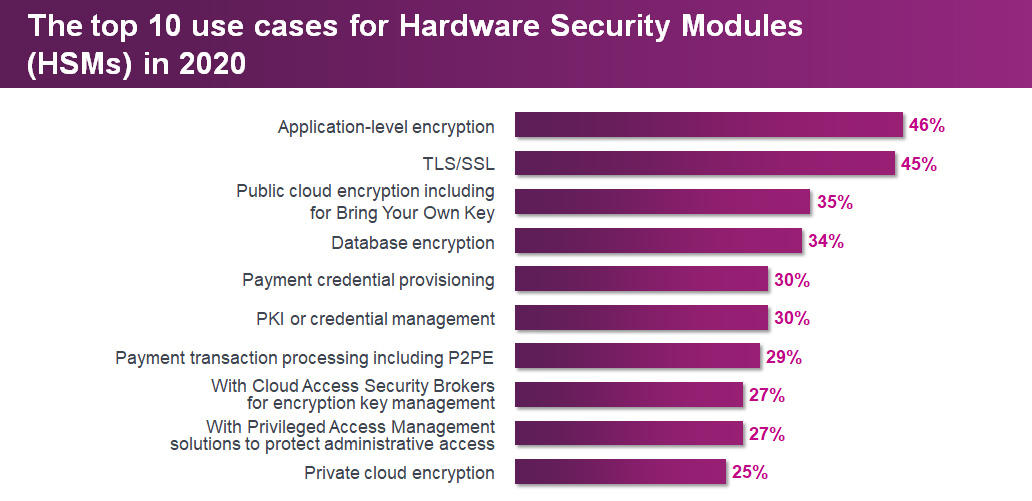
Today, the security needs of companies require that they have a high level of protection, particularly when it comes to data. It seems to be obvious that cryptographic operations must be performed in a trusted environment. In industries like the payment industry where you handle card data, data has to be encrypted in order to comply with PCI DSS. Here HSM is the best practice and a must. But from a purely technical perspective, an HSM is a very secure way to store cryptographic keys.
HSMs are built to protect cryptographic keys. Large-sized banks or corporate offices often operate a variety of HSMs concurrently. Key management systems control and update these keys according to internal security policies and external standards. A centralized design of key management brings the advantage of streamlining the management of keys and providing the best overview for the keys across many different systems.
The hardware is physically protected. You cannot break into it, and it detects and alerts you if something is wrong. If an HSM is stolen and gets switched off, the cryptographic keys can be automatically deleted from its memory. Thus, it is a secure solution if you need to protect extremely sensitive information.
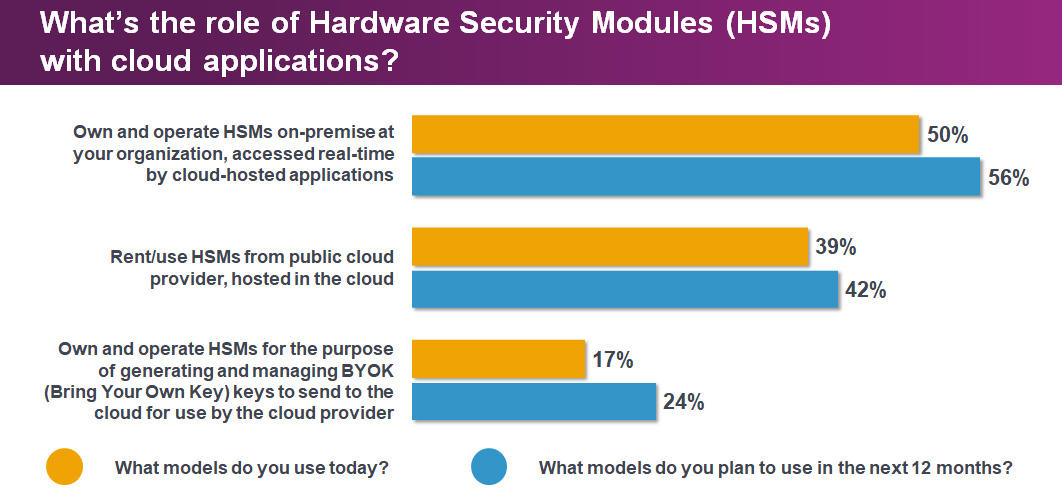
The primary purpose or use cases for deploying HSMs are application-level encryption, TLS/SSL, followed by public and cloud encryption including for BYOK and database encryption.
So, a hardware security module (HSM) is designed to provide an exceptionally high level of security to businesses in a variety of industries that need to safeguard their data. But what is an HSM, and what are the benefits of using one?
HSMs are devices specifically built to create a tamper-resistant environment in which to perform cryptographic processes (e.g., encryption or digital signing) and to manage the keys associated with those processes. These devices are used to protect critical data processing activities and can be used to strongly enforce security policies and access controls. The technology is trusted because it:
– Is built on top of specialized hardware. The hardware is well-tested and certified in special laboratories.
– Has a security-focused OS.
– Has limited access via a network interface that is strictly controlled by internal rules.
– Actively hides and protects cryptographic material.
HSMs enable organizations to:
– Meet and exceed established and emerging regulatory standards for cybersecurity, including GDPR, eIDAS, PCI DSS, HIPAA, etc
– Achieve higher levels of data security and trust
– Maintain high service levels and business agility
HSMs have outstanding and incomparable performance. It performs a small number of tasks, but does so very efficiently because it’s designed and optimized for such tasks. Security teams can gain the flexibility and efficiency they need, while maximizing security. With these offerings, organizations can establish secure, efficient and uniform control over their HSMs, operational policies and keys.
We invite you to ask more about protecting sensitive data and applications, on simple and efficient way, using on-demand cyprography. Contact us at – https://alfatec.hr/kontakt/