While there are many ways to protect sensitive data in databases, IT requirements for performance, availability and security can sometimes clash: will this security feature compromise database read and write performance?
Can I be certain that the encryption key will always be available for fast read performance?
Finding the balance between database security, availability and performance can lead to a close examination of which columns of the database contain sensitive data that must be protected versus those that might not. And this leads to the possibility of seeking a solution with column-level encryption granularity.
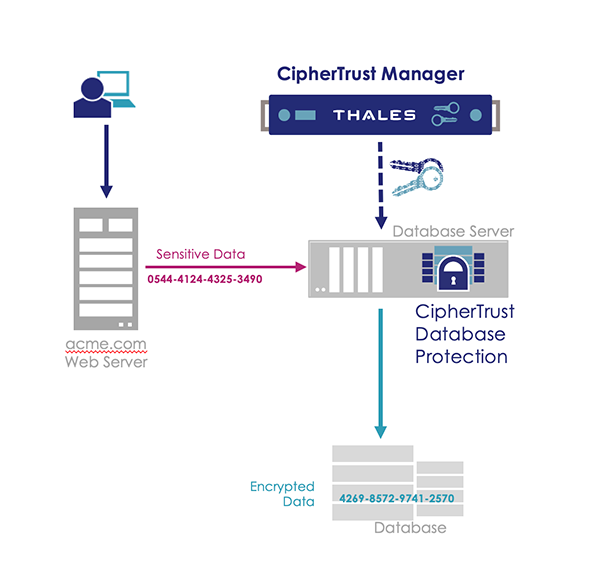
For your database security needs, consider CipherTrust Database Protection, a solution that can provide high-performance, column-level database encryption with an architecture that can provide high-availability to ensure that every database write and read happens at almost the speed of an unprotected database.
The goal of deploying CDP is to retrofit existing databases so that security can be provided by encrypting and decrypting the data flowing into and out of databases. Deployment starts with encrypting existing databases - a process called data migration.
Data migration is the process of encrypting existing column(s). It also involves altering existing tables so that they can store the resulting ciphertext, and creating views and triggers so that existing applications can seamlessly and automatically encrypt new data and request decrypted data when needed.
CDP ensures various levels of security to protect your data from unauthorized users. Once the data is migrated, users and applications must have permission to send a request from the database to the Key Manager and they must have permission to access the encryption key. If either of these conditions is not met, then the sensitive data is not accessed.
With CipherTrust Database Protection you will get:
Efficient Encryption
By focusing on specific database columns, CipherTrust Database Protection encrypts and decrypts data efficiently, in a fraction of the time required for an entire database. Format preserving encryption enables data analytics on encrypted data.
Secure Collaboration
A security solution is effective only if it both reduces business risks and meets organizational goals. Flexible encryption options with granular access controls enable organizations to avoid all-or-nothing approaches of other encryption solutions.
Cloud Friendly
CipherTrust Database Protection along with CipherTrust Manager may be deployed in cloud and virtualized environments so organizations can confidently pursue their cloud strategy. Even when data is in the cloud, organizations remain in full control of both their data and their encryption keys.
Achieve Compliance
CipherTrust Database Protection features comprehensive logging and auditing capabilities to enable organizations to track access to encrypted data and keys. As a result, one can effectively address internal policies and all relevant regulatory mandates, including encrypting personally identifiable information (PII) and other sensitive, confidential data to comply with privacy mandates such as, Payment Card Industry Data Security Standard (PCI DSS) and the Health Insurance Portability and Accountability Act (HIPAA).
Ask us for more information!