The urgent need for data-at-rest encryption continues to grow. Compliance requirements proliferate. Digital transformation expands attack surfaces. And every day we see new internal and external threats to critical IP, PII, customer and citizen information, and more.
Within this environment of increased risks to sensitive data, enterprises require the ability to limit access to sensitive information to only those users, groups, and processes that require the use of the data – and no more. What is required is a way to make sensitive data useless (and valueless) when not in use and then to control access to the levers that make the data useful again, when it is needed by a legitimate user.
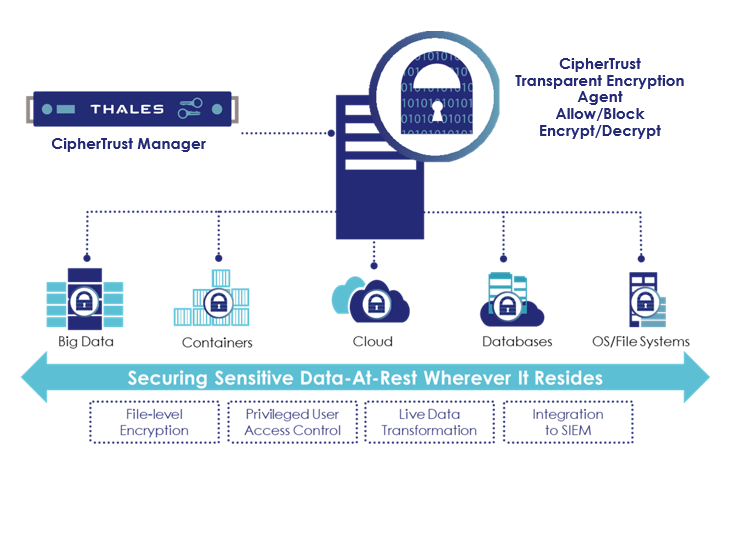
ALFATEC Group presents best tool for transparent encryption with user access control – CipherTrust Transparent Encryption. It delivers data-at-rest encryption with centralized key management, privileged user access control and detailed data access audit logging. This protects data wherever it resides, on-premises, across multiple clouds and within big data, and container environments.
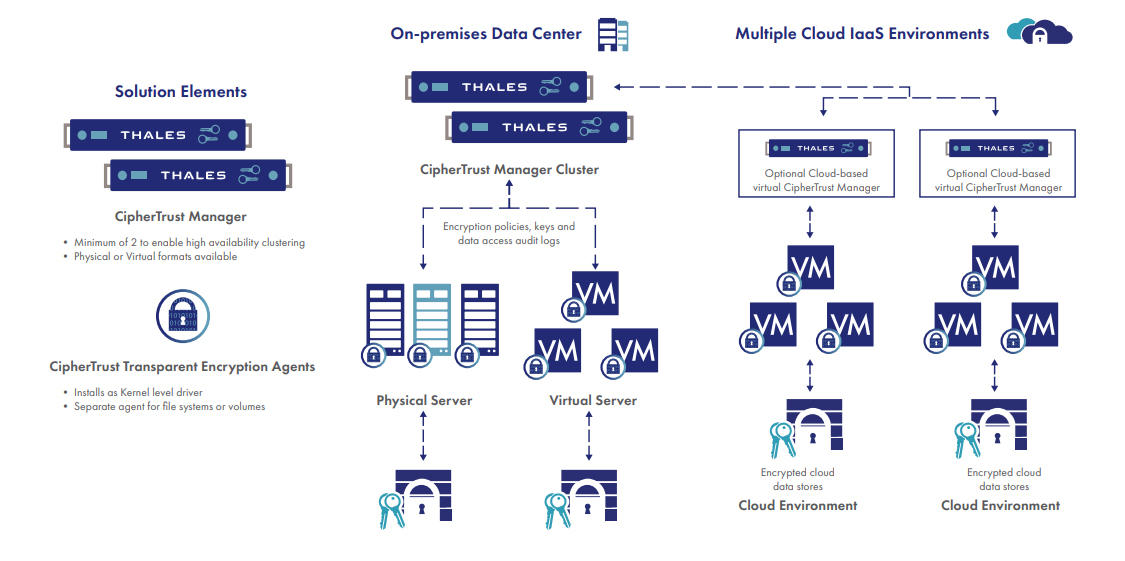
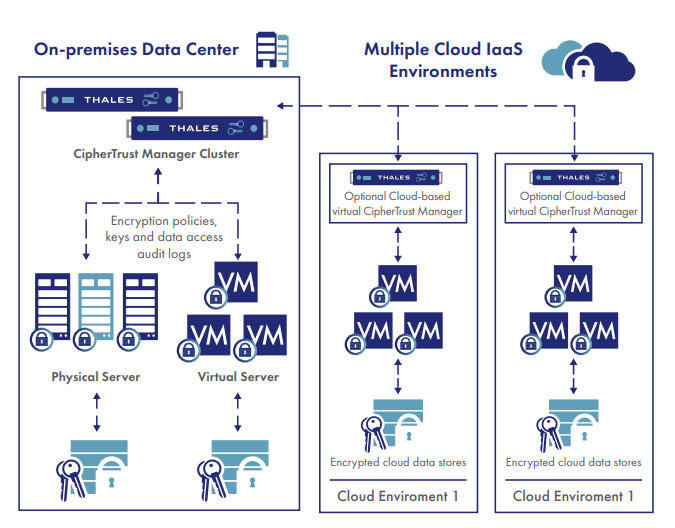
The deployment is simple, scalable and fast, with agents installed at operating file-system or device layer, and encryption and decryption is transparent to all applications that run above it. CipherTrust Transparent Encryption is designed to meet data security compliance and best practice requirements with minimal disruption, effort, and cost. Implementation is seamless keeping both business and operational processes working without changes even during deployment and roll out. The solution works in conjunction with the FIPS 140-2 up to Level 3 compliant CipherTrust Manager, which centralizes encryption key and policy management for the CipherTrust Data Security Platform.
Encryption, access controls, and data access logging are basic requirements or recommended best practices for almost all compliance and data privacy standards and mandates, including PCI DSS, HIPAA/Hitech, GDPR and many others. CipherTrust Transparent Encryption delivers the controls required without operational or business process changes.
The CipherTrust Transparent Encryption agent runs at the file system or volume level on a server. The agent is available for a broad selection of Windows, Linux, and AIX platforms and can be used in physical, virtual, cloud, container, and big data environments – regardless of the underlying storage technology. Administrators perform all policy and key administration through the CipherTrust Manager. Encryption takes place on the server, eliminating bottlenecks that plague legacy, proxy-based solutions.
Key features
– Transparent data protection. Continuously enforces file-level encryption that protects against unauthorized access by users and processes and creates detailed data access audit logs of all activities without requiring changes to applications, infrastructure, systems management tasks, or business practices.
– Seamless and easy to deploy. CipherTrust Transparent Encryption agents are deployed on servers at the file system or volume level and support both local disks as well as cloud storage environments, such as Amazon S3 and Azure Files.
– Define granular access controls. Apply granular, least-privileged user access policies that protect data from external attacks and misuse by privileged users. Specific policies can be applied by users and groups from systems, LDAP/Active Directory, Hadoop and containers. Controls also include access by process, file type, time of day, and other parameters.
– High-performance hardware accelerated encryption. CipherTrust Transparent Encryption only employs strong, standard-based encryption protocols, such as the Advanced Encryption Standard (AES) for data encryption and Elliptic Curve Cryptography (ECC) for key exchange. Encryption overhead is minimized using the AES hardware encryption capabilities available in modern CPUs.
– Comprehensive security intelligence. Identify and stop threats faster with detailed data access audit logs that not only satisfy compliance requirements, but also enable data security analytics. In addition, security intelligence logs and reports streamline compliance reporting and speed up threat detection using leading security information and event management (SIEM) systems.
– Broadest system and environment support. The agent is available for a broad selection of Windows, Linux, and AIX platforms and can be used in physical, virtual, cloud, container, and big data environments, regardless of the underlying storage technology.
As organizations continue to grow their infrastructure and data sets, they have to deal with a mix of in-house and cloud-based data assets and applications. Regardless of where this data is located, it requires the same level of data security and protection. CipherTrust Transparent Encryption enables enterprises to choose their implementation mode for data security based on their risk tolerance, compliance, and privacy requirements.
Couple of Use Cases examples
– Databases and Unstructured Files – Across Data Centers and Cloud Environments
A typical database protection scenario includes a CipherTrust Transparent Encryption agent deployed to database servers with a simple policy – a signed database process and the database user are allowed cleartext access to the protected data store, all others will only see file metadata and ciphertext. This effectively shields the database access from compromise by root and privileged user-based attacks, local system, and LDAP users and groups while also meeting compliance and best practice requirements for safeguarding the data set with encryption.
– Big Data
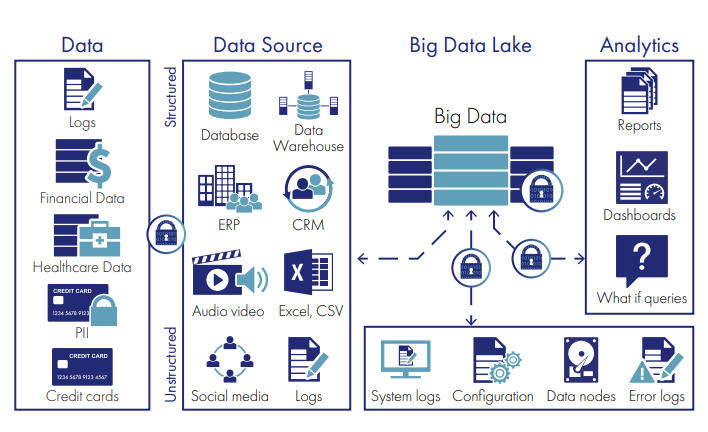
With nearly every enterprise embracing big data environments, and with large numbers of these environments implemented in the cloud, the security of the sensitive data within the data lake, source data environments, and the reports that hold high-value correlated results have become an insistent concern. CipherTrust Transparent Encryption safeguards this information. A typical deployment includes agents installed on compute nodes, source data servers, and servers accessing log/report repositories. Data is encrypted throughout the environment with appropriate access policies and data access logging controls provided by the CipherTrust Manager. Further, the use of hardware encryption capabilities in underlying compute infrastructure results in minimal overhead from encrypt/ decrypt operations. This makes it possible to use the solution even where speed and compute capability are critical.
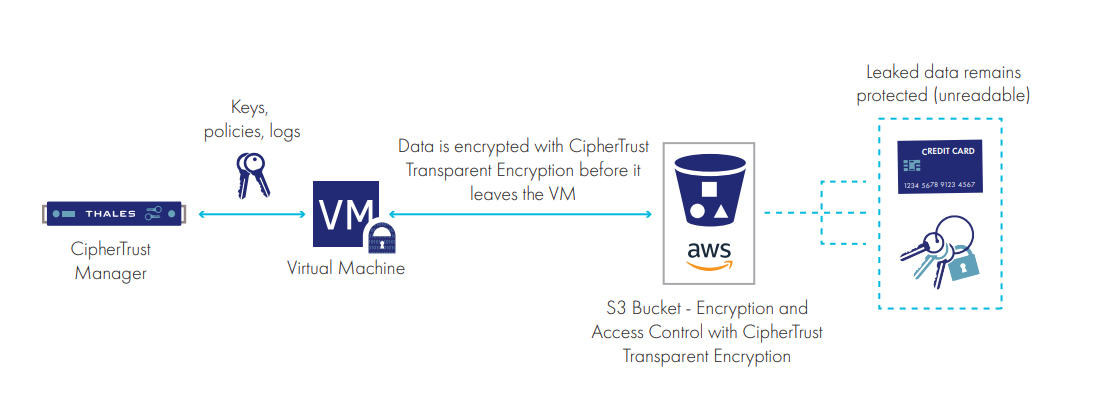
– Advanced data protection for Amazon S3
As organizations increasingly use Amazon S3 cloud storage as part of their implementation strategy, as well as for backups and failover environments, they need to protect data within these S3 buckets just as they would if the storage were located within their own data centers. With advanced data protection for Amazon S3, organizations can apply transparent encryption and access controls to sensitive data in S3 buckets. The CipherTrust Trasnparent Encryption solution encrypts unstructured files, semi-structured data, or structured databases before they are written to Amazon S3 buckets. This assures that the data is always encrypted in-flight, for example from on-premises hosts or Amazon EC2 instances to the S3 buckets.
Advanced capabilities:
– Zero-downtime data transformation. The Live Data Transformation option eliminates the downtime required for initial encryption and scheduled rekeying operations. This patented technology allows for databases or files to be encrypted or re-keyed with a new encryption key while the data is in use without taking applications off-line.
– Advanced access controls for big data (Hadoop). When implemented in Hadoop environments, access controls are extended to Hadoop users and groups.
– SAP HANA reviewed and qualified. SAP has qualified CipherTrust Transparent Encryption with HANA v2.0 to deliver data encryption, privileged user access control, and granular file access audit logs.
Please contact us for more information about CipherTrust Transparent Encryption!