Verizon recently released its 2021 Data Breach Investigations Report, with a clear indication that credentials are still a top attack vector and a primary target for hackers. Similarly, phishing—despite decades of experience and machine-learning-based innovation into email filtering—is still present as the number one crime action, according to the FBI. With this startling fact in mind, a question arises: what is phishing really all about? The goal is to gain credentials—in most cases, anyway.
The tremendous visibility gap within cloud security solutions—whether it’s CASB, Proxy, NGFW, or any similar approach—is derived from the lack of a complete, solid definition of SaaS services.
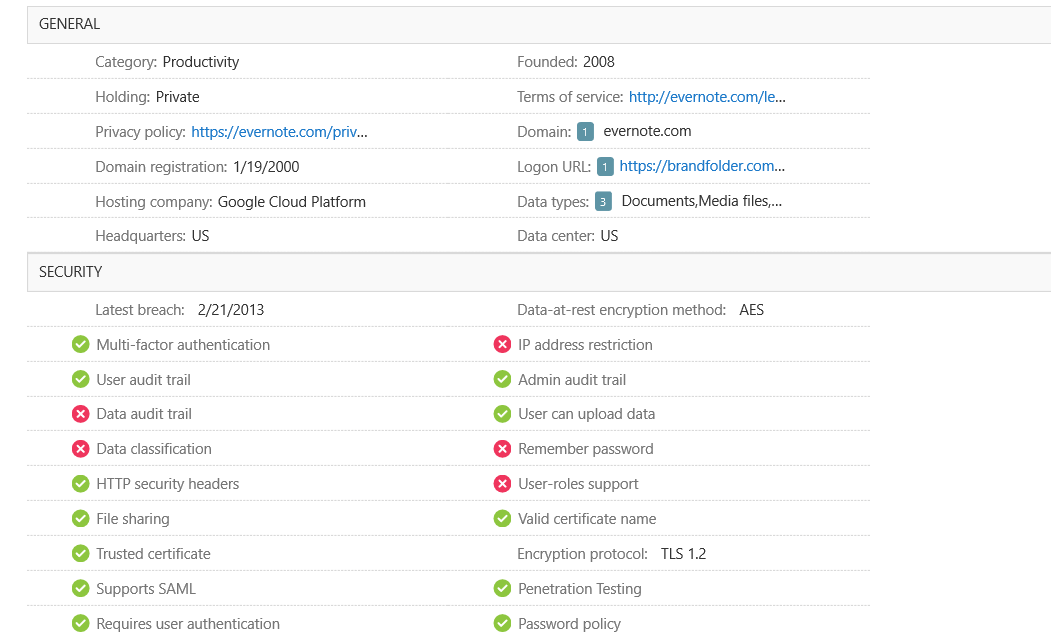
Microsoft CASB currently supports around 17,500 applications. Meanwhile, other market-leading vendors may support up to twice that amount, all advertising the ability to detect Shadow IT.
But what are these services, and what does it mean to “support” them? In all fairness, these databases likely fulfill their promise to cover most of the larger applications, such as O365, box.com, Salesforce, and thousands of other productivity sites. They accomplish this goal through a number of means: discovering their network traffic or URL, collecting endpoint logs— and for the really important services, connecting to them directly via API. For most organizations, however, API-based coverage is only affordable for perhaps a handful of large enterprise services, as they are sometimes locked behind a per-application cost.
These services are equipped with deep visibility into certain aspects of the applications. They may enable SSO services, DLP, or multi-factor authentication; furthermore, apps can be tagged as sanctioned, thus enabling the discovery of unsanctioned Shadow IT services.
So, how exactly does this fare in terms of protecting those valuable accounts and discovering employee-created passwords and processes? Firstly, it’s important to note that these are costly services requiring high maintenance. Therefore, SASE or zero trust penetration into all business segments is probably lagging behind when compared to legacy security solutions, such as firewalls or endpoint protection.
What’s more, these services are still lacking for the few businesses they empower. These solutions continue to barely scratch the surface, missing 99% of the web.
In 2020, there was an estimated 24 million e-commerce sites available.
That incredible number represents just one category. But are online stores, hotel booking sites, e-learning platforms, partner portals, and local government services considered to be SaaS? According to CASB vendors, absolutely not. Although there are tens of millions of websites providing valuable services utilized by various business departments, many of them are simply not considered to be important enough for CASB support. Furthermore, there is a disproportionate effort to categorize these sites, as they change so rapidly—especially because even managed solutions have a 60% turnover rate every two years. It is actually great news for businesses, that their employees are constantly looking for new and better services, and abandoning the less valuable ones.
This information presents a startling fact. CASB vendors (and all other less-specialized approaches) miss most of the internet, yet claim to have complete visibility into Shadow IT.
That’s not all. Although CASB solutions and their heavy integrations provide great visibility into that limited fraction of the web, they completely miss the most important factor: the credentials. No CASB vendor, endpoint, network, or API-based service is capable of discovering what accounts or passwords are being created or used, even on sites that are otherwise visible.
So much detail, nothing about credentials.
It’s true that SSO and MFA options are great for managed services. But 99% of the remaining web—otherwise known as the real Shadow IT—is completely unintegrated. Even if there are options for signups, it is always the employee’s decision to use corporate IDP, MFA, or even a password manager. All of these are simply opt-in services.
With this in mind, it’s no wonder that these solutions bring absolutely zero value to password leak prevention, password hygiene, or employee awareness about proper credential usage. It’s also unsurprising that attackers make use of the weakest link in corporate security: everything that the employees do without oversight.
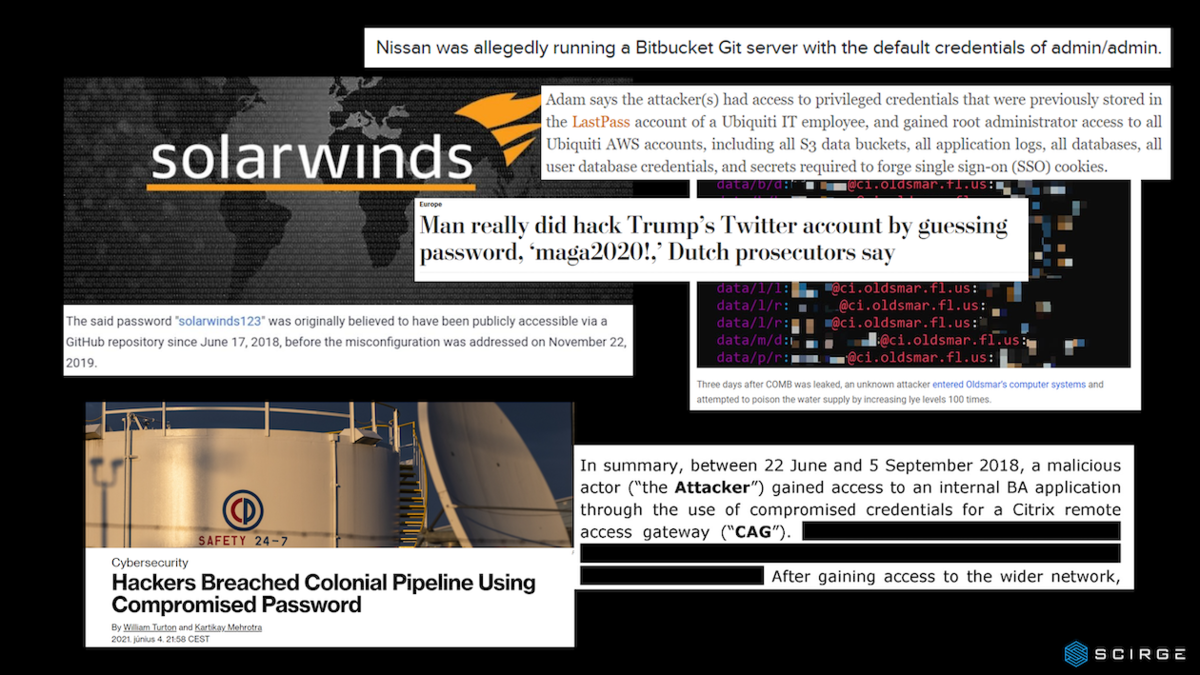
It goes without saying that SASE, ZTA, or CASB approaches are quite valuable and important. However, in order to battle Shadow IT and prevent account takeovers or negligent password usage—problems that led to some “small” incidents like the Solarwinds or British Airways hacks—there has to be a better solution.
To gain real visibility into Shadow IT, there are only a few key requirements:
Ability to identify every employee web login
The sites that are integrated with SSO and identity providers are not creating new passwords, so stolen credentials must be coming from somewhere else.
Check every single password used by employees for strength, reuse, breaches, and other hygiene controls.
Passwords that are reused (especially those from your AD accounts) pose a higher risk. Weak passwords are easier to attack, and passwords that get breached must be replaced—even if they were strong and sufficiently complex before.
Create inventories—for every employee and every application.
So that when they leave, you will know what accounts to take care of.
Create constant awareness for all employees based on their actions.
You cannot blame your employees for misguided compliance and proper account usage—that’s not their profession. But you can educate and warn them constantly, exactly at the time when they are at risk.
If you take care of the above factors, you can feel safe knowing that no invisible forces will undermine your otherwise hardened, beautifully-orchestrated networks with SASE, ZTA, and all other trending concepts behind them.
We thank Scirge for this insight.
Ask us for more information!