Electronic signatures have become increasingly strategic as a key element of digitalization. They help save money, reduce the need for physical meetings, and reduce paper usage in daily transactions carried out between citizens, consumers, employees, companies, and administrations.
The following regulations have already established a common legal framework for the use of electronic signatures that made them legally equivalent to handwritten signatures:
• European directive 1999/93/EC on electronic signatures
• ESIGN Act approved in the U.S. in 2000
• International electronic commerce law UNCITRAL of 2005
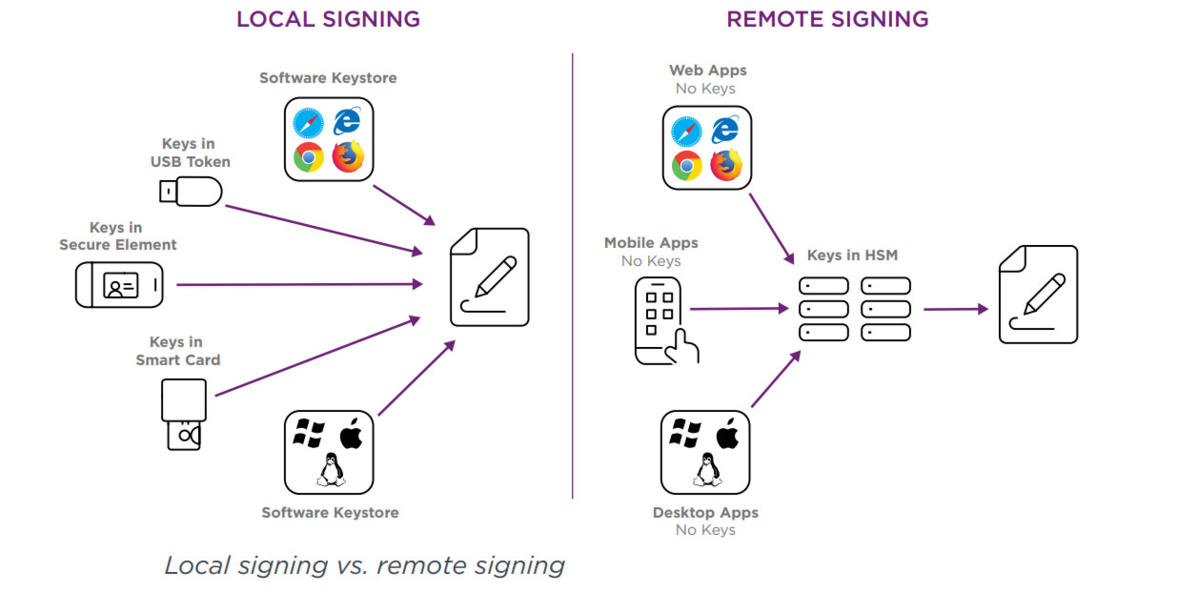
Signature Activation Module (SAM) offers remote digital signature services. It ensures that the Signer’s signing keys are only used under the sole control of the Signer and only used for the intended purpose.
The eIDAS Regulation introduces remote signing as a new use case. Remote signing centralizes keys and signing certificates on a server, while guaranteeing that the signer is the one who retains sole control of the signing key. Some of the benefits of remote signing are:
• Ease of use
• Centralized control and auditing
• Reduced costs at different levels, especially in deployment and integration
New signature types and formats Regulations and technical standards have established all the legal and technical elements necessary to deploy electronic signatures as well as conditions of interoperability. There are two types of electronic signatures:
• Electronic signature: made by individuals or natural persons
• Electronic seal: corresponding to the signature made by companies or legal persons Interoperable formats are standardized:
• PAdES for signing PDF documents
• XAdES for signing XML documents
• CAdES for signing binary files
And the entities and elements involved in the signing process are specifically detailed, such as the role of the trust service provider (TSP) and the qualified signature creation device (QSCD).
Entrust electronic signature solutions are based on PKI technology and digital certificates. This technology is widely adopted by the industry and has numerous applications in the field of security.
Plus, PKI technology is the basis for some authentication mechanisms used to gain access to the remote signature service, characterized by the high level of trust they offer and their contribution to fraud mitigation. A signing solution can implement or accept different authentication methods depending on:
• The adequacy of the level of trust
• The ease of use (or user experience) that is sought
• The type of business process involved
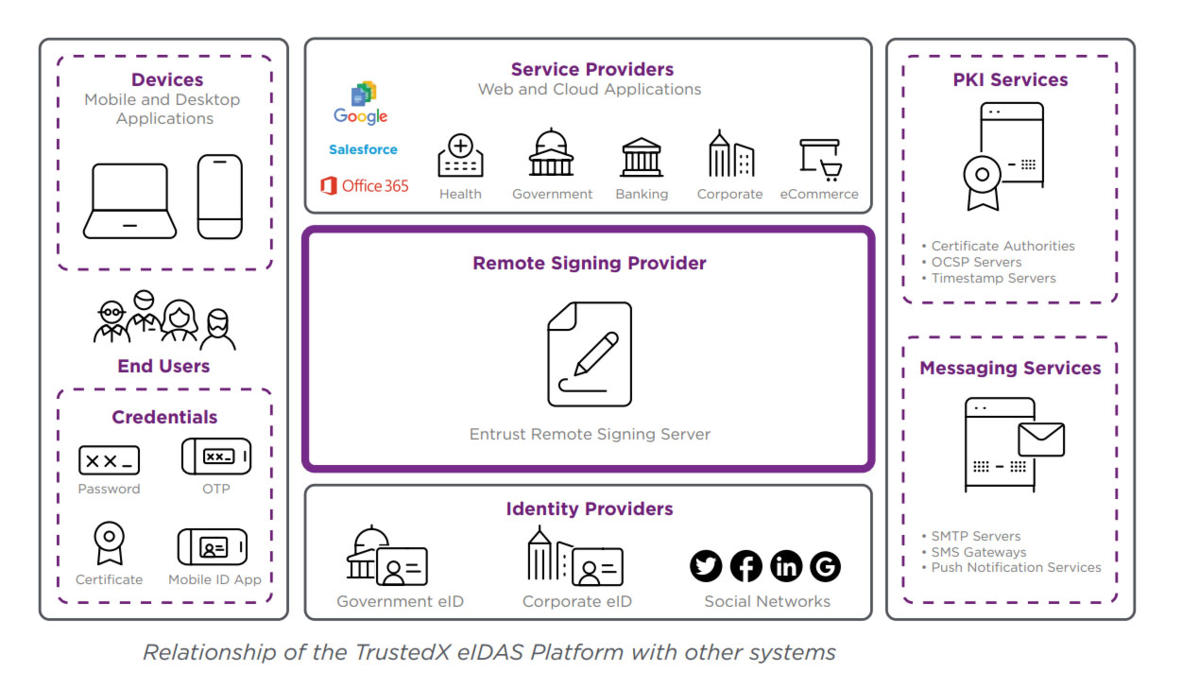
The remote signing service can be operated by a TSP to service applications from multiple organizations. These applications are the service providers, since they are ultimately the ones that end up providing the services to the end users.
Use cases and compatibility End-users consume the services offered by the service providers. In the field of public administration, end-users are citizens or public employees, and service providers are the applications of different ministries or municipalities.
In the private enterprise environment, end-users are clients or employees of the company, and service providers are the corporate applications that they use. Today it’s common for end-users to access services from a variety of different devices, and in a variety of different ways:
• Mobile applications (e.g. devices using iOS or Android operating systems)
• Desktop applications (e.g. computers using Windows, Mac, or Linux operating systems)
• Directly from a browser without the need to install any software
Benefits of Remote Signing Server:
• Streamlined application development and mobility: Helps develop use cases with widely used integration mechanisms, offering a complete set of REST APIs for developers. It also can be used for other use cases, such as cloud services or applications on mobile devices.
• Improved user experience for end users/citizens: User-friendly features such as mobile applications and web applications don’t present barriers and don’t require software installation on the user’s computer.
• Identity fraud protection: Recognizes the level of assurance (LoA) of the identities verified by each identity provider, as recommended by the European regulation eIDAS, the OMB/NIST 800-63 recommendation in the U.S., or the ITU-T X.1254 and ISO standards/IEC 29115.
The level can be stepped up by requesting the user to provide additional authentication factors when necessary, with the possibility to trigger the step-up for each signing operation.
• Stronger branding: Customizable user elements such as web interfaces and a mobile app for signature activation help support brand development.
• Compliance with the most recent regulations: Serves as a technological framework for deploying applications and services based on signature regulations, which, in some countries, have been recently reviewed and updated
Ask us more about digital signatures!