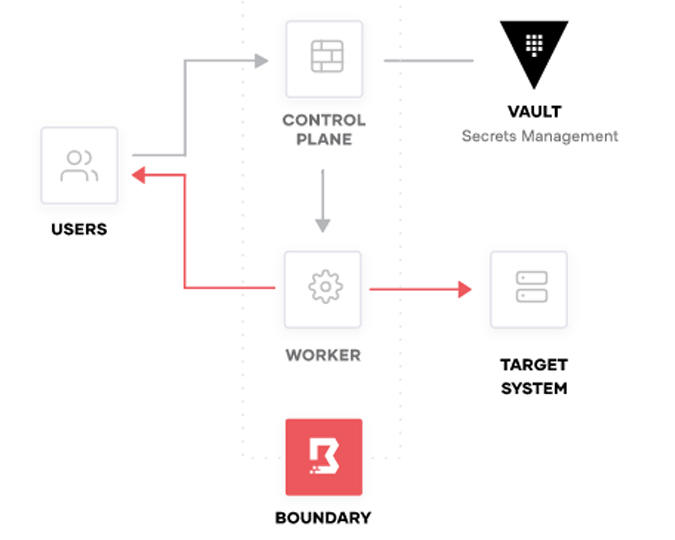
HashiCorp Boundary is a secure remote access solution that provides an easy way to allow access to applications and critical systems with fine-grained authorizations based on trusted identities. Across clouds, local data centers, low-trust networks, Boundary provides an easier way to protect and safeguard access to application and critical systems by trusted identities without exposing the underlying network.
Anyone who works in Dev, DevOps, SecOps or Ops have similar rhythm:
– starting VPN
– SSH or remote desktop to a few servers
– check internal monitoring websites
Sometimes this involves MFA, and solid encryption in transit. The problem is when new colleagues join organization and gets access to all these services or worse that they still had access after they moved on to a new job.
This is where Boundary comes in. It provides a TCP proxy layer in front of all your services and a consistent way to authenticate to that proxy layer before it decides to grant access to the requested service. It also solves the discovery problem that arises as your infrastructure grows. Also, Boundary’s Controller and you can find all the services and hosts.
Boundary supports Windows, MacOS and Linux as client platforms, with both a command line and a browser user interface.
Traditional Workflow
To better understand how Boundary works, and why we are building it, we want to provide a few examples that highlight the challenges users and operators face when securely connecting to applications and critical systems.
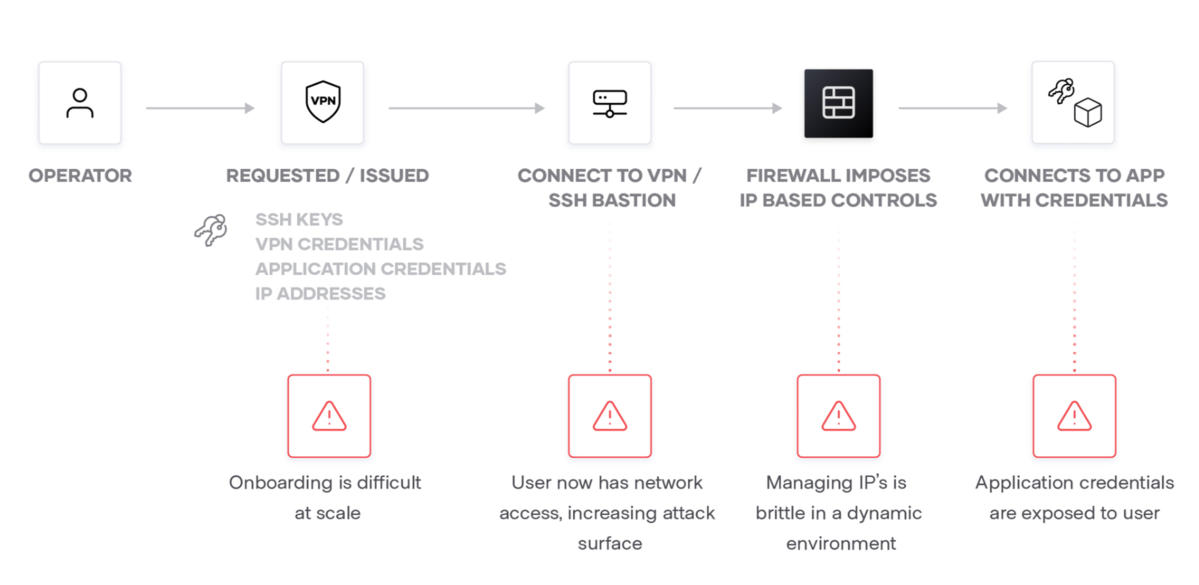
The diagram below illustrates a typical connection workflow and the challenges that occur when a user requires remote access to a production system located in a private network. Usually a gateway bridges access into these private networks through a VPN or SSH bastion host. Both solutions offer varying degrees of security which could provide a user with direct access on the private network and not just access to the intended systems.
This traditional access model assumes resources are mostly static, and it is not well suited for the cloud with highly ephemeral and dynamic environments. Scaling the solutions as workforces and infrastructure grow creates additional pain points and complexity for administrators to manage.
Once users are on these private networks, they can access any system and not just the intended target. If the credentials used to access the VPN or SSH host are lost or stolen, an adversary could access the entire network. To safeguard against that risk, a traditional workflow will typically place a firewall inside these private networks that restricts what users have access to in order to safeguard against this risk.
However, managing internal firewalls is time consuming and wasteful when the system granting access should have followed the principle of least privilege from the outset. Boundary was designed with these core problems in mind: grant access to critical systems with least privilege.
This product greatly simplifies resources access management in organizations. Access to instances can be managed simply by adding or modifying the permissions that a user has, without having to distribute ssh keys, perform manual operations on the machines, etc.
In summary, this product gives a new way to manage access to different resources. Not only through SSH, but it will be a way to manage access through roles to machines, databases, portals, etc. minimizing the possible attack vector when permissions are given to contractors. In addition, it is presented as a free and open source tool, which will not only integrate very effectively if you have the Hashicorp ecosystem deployed, but will also work seamlessly without the rest of Hashicorp’s tools.
Ask us more about HashiCorp Boundary!