Ransomware is a vicious type of malware that cybercriminals use to block companies and individuals from accessing their business critical files, databases, or entire computer systems, until the victim pays a ransom. It is a form of cyber extortion.
Cybersecurity Ventures predicts that a business will fall victim to a ransomware attack every 11 seconds, and the estimated cost to businesses globally will be around $20 billion by 2021. The direct costs can be attributed to the ransom demands — if the victim chooses to the pay the ransom — while the indirect costs are associated with the downtime, data recovery, lost revenue, improvements to cyber defenses, and reputational damage to the company.
Examples of Recent Ransomware
– Europe’s largest private hospital chain operated by Fresenius Group was hit by the Snake ransomware attack. They are a major provider of kidney dialysis machines and services to the largest hospitals across Europe and United States, which are in high demand during the Covid-19 pandemic. The intruders were holding their IT systems and data hostage in exchange for payment in a digital currency, such as bitcoin.
– The Sodinokibi group allegedly hacked into Grubman Shire Meiselas & Sacks (GSMLaw), based in New York, using Sodin and REvil ransomware. They not only encrypted all the legal documents of the law-firm but also threatened to release sensitive data that included contracts, phone numbers, personal correspondence, and non-disclosure agreements of their big-name clients (such as Robert DeNiro, Lady Gaga, Elton John, and many more), if ransom was not paid.
– Australia’s logistics giant Toll Group suffered a second ransomware attack within three months. A new strain of ransomware known as Nefilim gained privileged access using a brute-force password attack to systems that were running remote desktop protocol (RDP) services. The intruders demanded a double-extortion by not only encrypting the users’ files but also threatened to publish the data online through name and shame tactics.
Anatomy of a Ransomware Attack
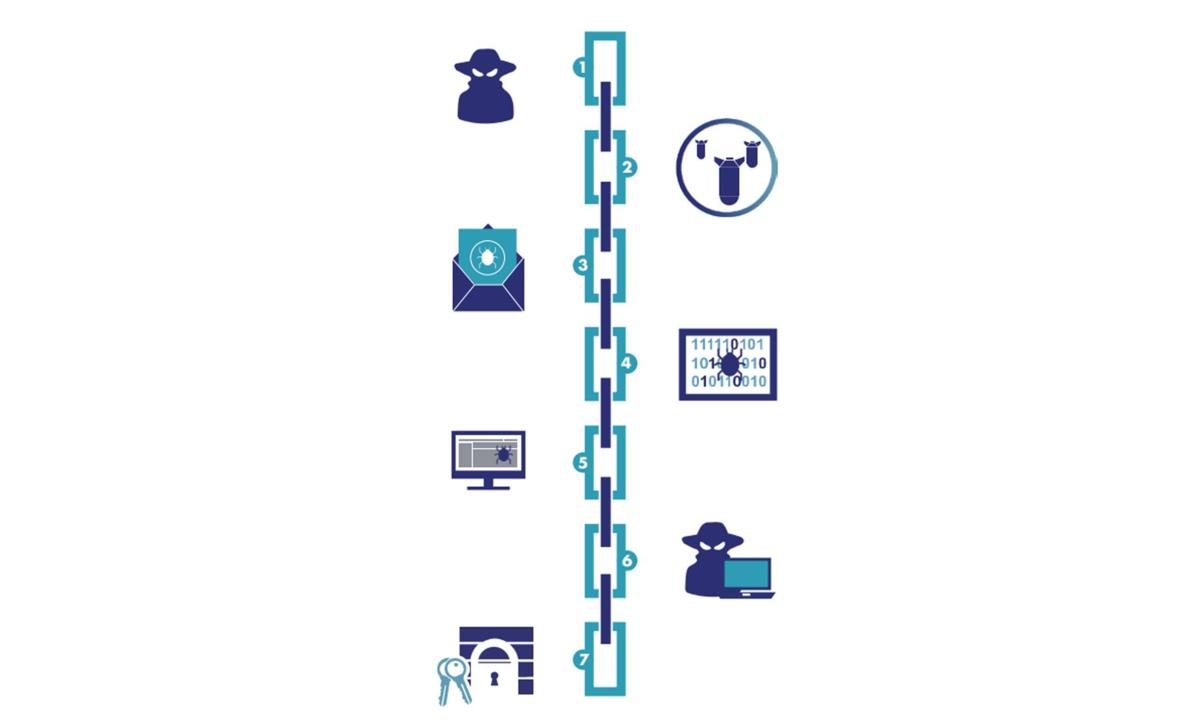
One typical Cyber Kill Chain shows seven stages of a targeted ransomware attack. It provides visibility into the intruders’ tactics, techniques, and procedures (TTPs).
Step 1: Reconnaissance – intruder harvests email addresses of all the employees in a company and prepares to launch a phishing campaign.
Step 2: Weaponization – intruder uses a ransomware kit purchased off the dark web tailored to deliver that malware through an email attachment.
Step 3: Delivery – intruder delivers the ransomware through a fake email as the payload or through a remote desktop protocol (RDP) service.
Step 4: Exploitation – When an employee unknowingly opens the fake email attachment, the malware exploits a known vulnerability and infects their laptop.
Step 5: Installation – The ransomware installs as a binary, which opens an access point (backdoor) to communicate with a command and control site.
Step 6: Command and Control (CnC) – Ransomware sends target host IP address and gets encryption key needed for encrypting all files and databases.
Step 7: Action – Ransomware exfiltrates sensitive documents to the CnC server and then encrypts those files and databases. It then displays a ransom note to the end user.
To effectively block any unknown malware (ransomware binaries) from taking your data hostage, security organizations need a robust data security solution that can provide the following capabilities:
– Application Whitelisting that identifies “trusted applications” – binaries which are approved to perform encryption/ decryption of business critical files. It also needs to provide a way to check the integrity of these applications with signatures to prevent polymorphic malware from getting into approved binaries.
– Apply Fine-grained Access Controls to your business critical data, which defines who (user/group) has access to specific protected files/folders and what operations (encrypt/decrypt/read/write/directory list/execute) they can perform.
– Data-at-rest Encryption protects data wherever it resides in on-premises data centers or in public/private clouds. This makes the data worthless to intruders when they steal business sensitive data and threaten to publish it, if the ransom is not paid. In addition, some ransomware selectively encrypts files so that it doesn’t take systems entirely offline.
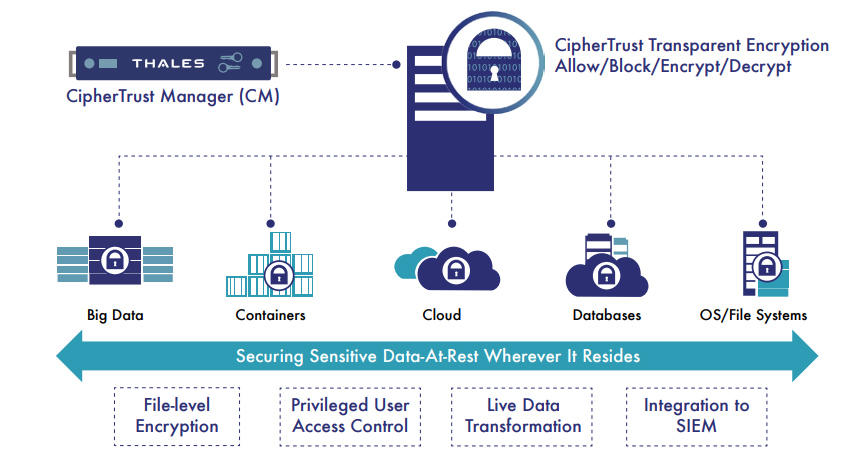
How Does CipherTrust Transparent Encryption Prevent Ransomware Attacks
ALFATEC Group recommend protecting your data with CipherTrust Data Security Platform from Thales. They unify data discovery, classification, data protection and unprecedented access controls with centralized key management – all in a single platform.
CipherTrust Transparent Encryption is one of the widely deployed data protection products within the CipherTrust Data Security Platform. It provides data-at-rest encryption, fine-grained access control and application whitelisting capabilities, enabling organizations to prevent ransomware attacks. It protects both structured and unstructured data with policy-based access controls to files, volumes, databases, containers, big-data wherever it resides on-premises and in hybrid cloud environments.
Access policies can be defined to create a whitelist of “trusted” applications to prevent any untrusted binaries (e.g. ransomware) from accessing data stores protected by CipherTrust Transparent Encryption and to prevent privileged users from accessing user data in files and databases. These access policies can enable you to block any rogue binaries from encrypting files/databases, even if the intruder has execute permissions for that binary and read/write permission to the target file that contains business critical data.
When it comes to data security, organizations are faced with an increasing number of decisive moments. Whether the moment is building an encryption strategy, moving to the cloud, or meeting compliance mandates, you can ask us for an advice!