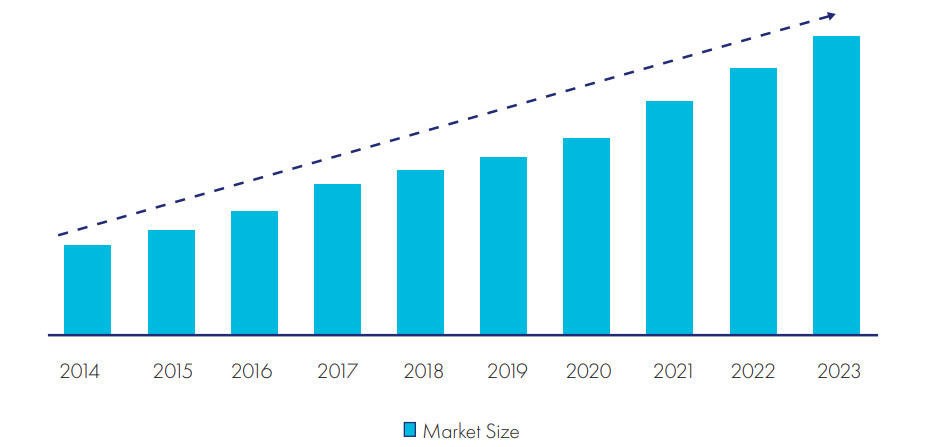
The rise of e-commerce enabled corporate organizations and banks to more easily expand their businesses and services around the world.
Online services, like e-banking, raise the need for encryption, decryption and strong authentication between identities and applications. For these purposes, enterprises deploy HSMs for the protection of clients and business transactions.
And it’s not just the digitized bits of information associated with individuals that are at risk of exposure when in the hands of business and governmental entities. These entities have their own set of sensitive and valuable information that is at risk when in digitized form, for example: operational information such as business and marketing plans, customer account information, price lists, and financial statements; tactical and strategic plans to protect and serve a citizenry; and various forms of intellectual property.
Considering the growing exposure and potential ramifications of information incidents – such as failed regulatory audits, fines, litigation, breach notification costs, market set-backs, brand injury, and even business failure – business and governmental entities are wise to plan and implement a comprehensive information risk management strategy. A growing number of entities are proactive in this regard and have integrated Hardware Security Modules (HSMs) into their information risk management deployments. In fact, for some entities, HSMs are instrumental in the development of innovative products and services that are only possible through secure storage and use of digitized information.
HSM
In general, Hardware Security Modules (HSMs) are dedicated systems that physically and logically secure cryptographic keys and cryptographic processing.
Functions supported by HSMs include:
• Life-cycle management of cryptographic keys used to lock and unlock access to digitized information.
• Cryptographic processing which produces the dual benefits of isolating and offloading cryptographic processing from application servers.
Corresponding to the increase in market demand for HSMs has been a continuous expansion in HSM features and performance characteristics to address a wider array of use cases. In addition, the comparative differences between HSMs and software-based alternatives have gained clarity.
HSM vs. Software
Routinely IT is faced with a decision on whether purpose-built appliances are preferable to software. Purpose-built appliances represent another piece of physical hardware for the IT organization to procure, deploy, configure, and maintain. More devices add to the capital expenditure budget, add to overall IT complexity. With IT organizations already struggling with sizable and diverse hardware inventories, and keen to reduce their carbon footprints, a “more specialized hardware” approach may not always be the default choice. Software, by contrast, has the advantage of installing and running on potentially existing and dormant servers and can ride the wave of improving server price performance and energy efficiencies. Consequently, software, at least initially from financial, IT operational, and carbon footprint perspectives, appears to be a worthy alternative to purpose-built appliances.
This view of hardware versus software, however, has proven to be less robust when the function in question is security. HSMs represent a crucial element in protecting digitized information. Attempting to accomplish the same in software should not be done without fully considering the implications.
HSMs are fully contained solutions for cryptographic processing, key generation, and key storage. As purpose-built appliances, they automatically include the hardware and firmware (i.e., software) necessary for these functions in an integrated package. Physical and logical protection of the appliance is supported by a tamper resistant/evident shell; and protection from logical threats, depending on the vendor’s products, is supported by integrated firewall and intrusion prevention defenses.
Some HSM vendors also include integrated support for twofactor authentication. Security certification is typically pursued by HSM vendors and positioned as a product feature. Software for these same functions is not a complete out-of-the-box solution. Server hardware is a separate purchase, unless unused servers are present, as is firewall, intrusion prevention, and two-factor authentication. Being tamper resistant is not a trait typically associated with general-purpose servers. Security certification encompassing the combination of hardware platform and software would be the responsibility of the user organization and can be a lengthy and very costly activity, especially if involvement with certification bodies is not standard operating practice for the organization using the software.
HSMs provide organizations with the unrivaled security benefits of a hardware boundary that delivers physical and logical protection that software alone simply cannot match. Further, by offering centralized key storage, scalable cryptographic processing, and robust security mechanisms surrounding backup and restore, HSMs significantly streamline security administration. As businesses and governments seek to leverage these proven strengths, security architects will only grow more reliant upon HSMs—both to guard against evolving threats and to capitalize on the emerging opportunities posed by technological advances.
Ask us for more information about HSMs!