Encryption key management is the administration of tasks involved with protecting, storing, backing up and organizing encryption keys. High-profile data losses and regulatory compliance requirements have caused a dramatic increase in the use of encryption in the enterprise.
For that reason is crucial to prevent unauthorized access to sensitive information—if keys are compromised, entire systems and data can be compromised and rendered unusable until the situation is resolved. Different industries have different requirements for key management.
As organizations deploy ever-increasing numbers of encryption solutions, they find themselves managing inconsistent policies, different levels of protection, and experience escalating costs. The best way through this maze is often to transition into a centralized encryption key management system. In this key management case, and in contrast to the use of hardware security modules (HSMs), the key management system performs only key management tasks, acting on behalf of other systems that perform cryptographic operations using those keys.
The benefits of a centralized key management system include:
Unified key management and encryption policies
System-wide key revocation
A single point to protect
Cost reduction through automation
Consolidated audit information
A single point for recovery
Convenient separation of duty
Key mobility
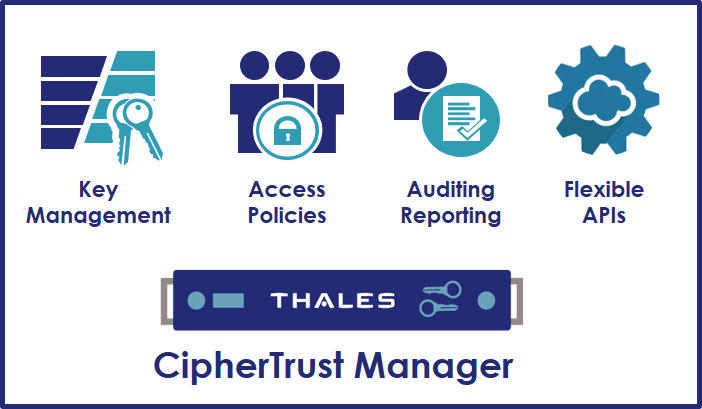
CipherTrust Manageroffers the industry leading enterprise key management solution enabling organizations to centrally manage encryption keys, provide granular access control and configure security policies.
CipherTrust Manager is the central management point for the CipherTrust Data Security Platform. It manages key lifecycle tasks including generation, rotation, destruction, import and export, provides role-based access control to keys and policies, supports robust auditing and reporting, and offers developer friendly REST API.
CTM is available in both virtual and physical appliances that integrates with FIPS 140-2 compliant Thales Luna or third-party Hardware Security Modules (HSMs) for securely storing keys with a highest root of trust.
These appliances can be deployed on-premises in physical or virtualized infrastructures and in public cloud environments to efficiently address compliance requirements, regulatory mandates and industry best practices for data security.
With a unified management console, it makes it easy to set policies, discover and classify data, and protect sensitive data wherever it resides using the CipherTrust Data Security Platform products.
Ask us for personal demonstration of Thales CipherTrust Manager!