Cryptography is defined as providing means of solution for protecting and controlling data wherever it exists.
Whenever cryptography is used, the risk in the content of data is transferred to cryptographic keys used to protect the data.
Key management refers to the management of cryptographic keys in a cryptosystem. This includes dealing with the generation, exchange, storage, use, crypto-shredding (destruction), and replacement of keys. It includes cryptographic protocol design, key servers, user procedures, and other relevant protocols.
Thales Key Management offerings streamline and strengthen key management in cloud and enterprise environments over a diverse set of use cases. Leveraging FIPS 140-2-compliant virtual or hardware appliances, Thales key management tools and solutions deliver high security to sensitive environments and centralize key management for home-grown encryption, as well as third-party applications.
This gives a greater command over the keys while increasing data security. Thales key management products connect with the applications through standard interfaces and deliver access to robust key management functions.
Need For Cryptography In Cloud
Cryptography In Cloud allows us to determine the level of granularity that is used to encrypt data. It set keys to automatically rotate regularly and uses a new primary version every time to encrypt data and limit the scope of data accessible with any single key version.
Great Management over key use: Manage Cloud Integrated Access Management permissions (IAM) for user-level permissions on every individual key and also grant access to both individual users and service accounts.
Easy Encrypt and sign-in In data: Cloud-hosted Key Management Service(KMS) gives users the flexibility to encrypt data with the use of either a symmetric or asymmetric key that is controlled by the user. It also helps users to perform sign-in operations with both RSA and elliptic curve keys of various lengths.
Thales Cloud key management solution is used to control the keys and thereby make the sensitive data and the workloads in the cloud run securely. This encryption and key management in the cloud can provide the same high-level protection as if it were fully on-premises and thereby, making organizations to reach new levels of efficiency and security.
Thales Cloud Key Management Solutions
Hardware Security Module (HSM) provides highly assured protection to the cryptographic keys used by applications across cloud-enabled and on-premises environments. With the use of Thales Network HSMs, organizations can protect the entire key life cycle on a centralized platform and leverage a single point of audit for cryptographic keys.
Features of Thales Key Management Solution
Strong Key Encryption Security: It provides the Security of Vormetric Data Security Manager to create keys and store them with FIPS 140-2 security. It can control full key metadata control during upload and for keys.
True Multi-cloud Support: Key Management as a Service keeps you in control of encrypted data with the use of Amazon Web Services, Microsoft Azure, Microsoft Azure Stack, Microsoft Azure, and Salesforce.com.
Automated Key Rotation: Keys are marked for automated key rotation on a per-cloud schedule with the use of API requests.
Comprehensive Key Management: It is meant to deploy Key Management as a Service with any number of keys already created at your cloud provider.
Federated User Access to Key Management: It is used to access a full range of logs and reports for fast compliance reporting.
Benefits of Thales Key Management Solution
Protect data Anywhere: Thales data protection solutions prevent unwanted access to keys on protected data, and thereby also the data that is protected by those keys, no matter the environment, is kept protected even by third-party cloud infrastructure providers.
Complete Control: This complete control enables you to own and control encryption keys in any environment to assure to have complete control of keys, and therefore the data too. This is used to achieve and maintain compliance with mandates such as PCI DSS (Payment Card Industry Data Security Standard).
Cloud agnostic: It supports many deployment scenarios, starting from on-premises data centers to private, hybrid, public, and multi-cloud environments. Thales key cryptography provides a tremendous amount of flexibility because enables customers to move keys in and out of cloud environments.
Scalability: Scalability provides means to the organization and its developers to optimize its infrastructure without any need to customize applications to support a multi-cloud deployment scenario.
Thales key management includes the following products:
CipherTrust Manager
CipherTrust Manager offers the industry-leading enterprise key management solution enabling organizations to centrally manage encryption keys, provide granular access control, and configure security policies. CipherTrust Manager is the central management point for the CipherTrust Data Security Platform. It manages key lifecycle tasks including generation, rotation, destruction, import, and export, provides role-based access control to keys and policies, supports robust auditing and reporting, and offers developer-friendly REST API.
CipherTrust Manager is available in both virtual and physical appliances that integrate with FIPS 140-2 compliant Thales Luna or third-party Hardware Security Modules (HSMs) for securely storing keys with the highest root of trust. These appliances can be deployed on-premises in physical or virtualized infrastructures and in public cloud environments to efficiently address compliance requirements, regulatory mandates, and industry best practices for data security. With a unified management console, it makes it easy to set policies, discover and classify data, and protect sensitive data wherever it resides using the CipherTrust Data Security Platform products.
Data Security Manager
The Vormetric Data Security Manager (DSM) is the central management point for all Vormetric Data Security Platform products. The DSM not only creates, stores, and manages the encryption keys that protect data, but it also enables organizations to manage every aspect of their Vormetric data security platform implementation. The Data Security Manager allows administrators to specify data access policies, administer DSM users and logical domains, generate usage reports, register new hosts, access security logs, manage third-party keys, digital certificates, and more. Moreover, as enterprises and service providers need data security management in concert with their other infrastructure, the DSM also provides integration capabilities with multiple APIs and a command line interface as well as a simple graphical user interface (GUI) operation.
CipherTrust Cloud Key Manager
As a convenience to their customers, Cloud Service Providers (CSPs) increasingly offer vendor-specific encryption and key management services. As a necessity for our customers, we offer vendor-independent encryption and key management services. We collaborate and innovate with CSPs and our customers to increase efficiency and operational resiliency across vendors in the cloud and on-premises.
We develop products for you, always focused on the fact that as Cloud consumers, you are responsible for the security of your data stored and used in vendor clouds. CipherTrust Cloud Key Management (CCKM) protects your time as well as your data with a single pane of glass view across regions for cloud-native, BYOK, and HYOK keys and one straightforward UI to manage all cloud Key Management Services.
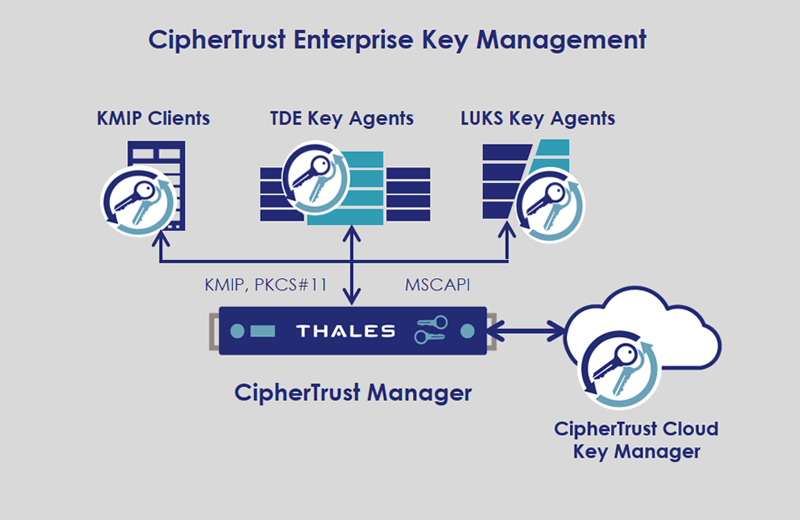
Enterprise Key Management
It is costly and complex for IT organizations to protect data using multiple encryption technologies across disparate data silos, such as file servers, databases, virtual environments, and cloud storage.
Enterprise Key Management solutions from Thales, enable organizations to centrally manage and store cryptographic keys and policies for third-party devices including a variety of KMIP Clients, TDE Agents on Oracle and Microsoft SQL Servers, and Linux Unified Key Setup (LUKS) Agents on Linux Servers. CipherTrust Enterprise Key Management delivers a robust, standards-based platform for managing encryption keys to protect data in disparate storage repositories across the enterprise. It simplifies the administrative challenges around encryption key management to ensure that keys are secure and always provisioned to authorized encryption services.